Update: The Phish Goes On - 5 Million Stolen Credentials and Counting
June 16, 2022
When PIXM’s threat research team first broke the news of a large-scale phishing campaign that had successfully stolen millions of credentials from legitimate Facebook users, we expected that perhaps the adversary would shut down the campaign, or at least change some of the elements to make it harder for us to detect and track. Much to our surprise, we have only seen the campaign continue to flourish undeterred and still detectable.
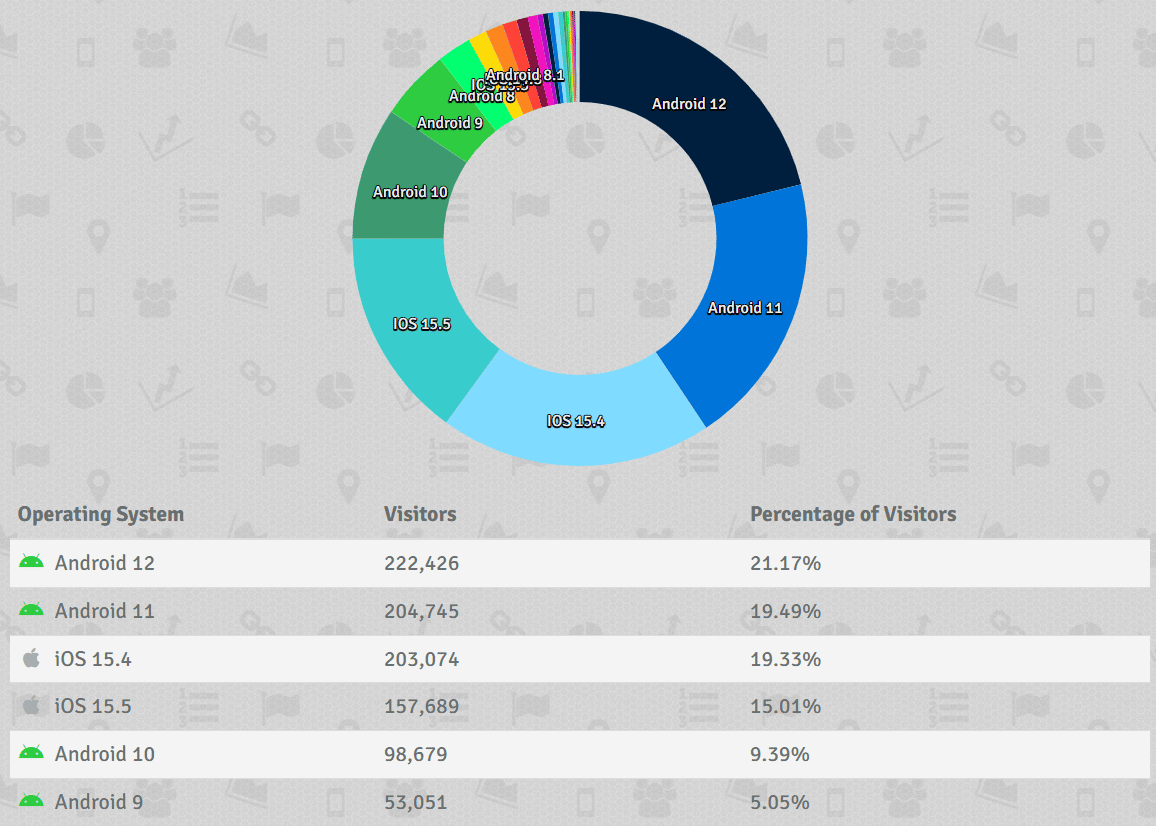
We are continuing to see new phishing pages and new domains associated with this campaign literally every day. Most of the new visitors to these domains are coming from mobile browsers (an example from the attackers’ actual traffic monitoring dashboard shown below), and we believe the primary target vector is Facebook Messenger on mobile devices. We estimate at least 400 unique domains to be in circulation currently, with many of them seeing at least a million visitors (not all will have had their credentials stolen, but a not insignificant number did.). Our initial story posited that at least a million Facebook credentials were stolen through this attack. We now estimate that number to be at least 5 million, and possibly much higher.
The targeting of mobile devices make this attack particularly nefarious, as mobile platforms generally offer little to no protection from phishing attacks that originate outside of email. We are picking these up when they are blocked by PIXM Mobile, which detects and stops such attacks in real-time. However, few products offer such protection, leaving most targets completely vulnerable.
PIXM’s research team has reported this incident to the FBI and Interpol, and we have no further comment on the law enforcement elements of the investigation.
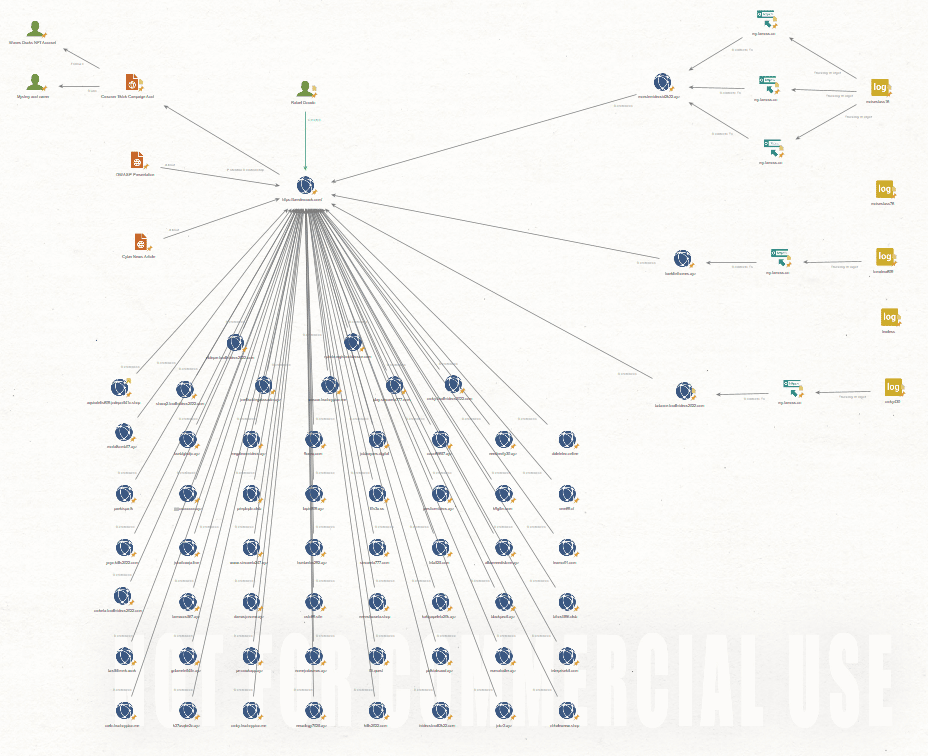
The below image highlights the scope of this campaign, by tracking the connections between a small subset of the domains in use.
Avoiding Detection: Evasive Techniques
Since originally publishing our findings on this large-scale campaign, we have noticed some evolution in the adversaries strategy: the adversary is now using a novel technique to avoid detection by traditional anti-phishing tools, and to avoid having their phishing links end up on threat intelligence feeds. Instead of taking the target directly to a phishing page to enter their credentials, the pages that are being sent to potential victims now temporarily load a benign-looking shopping cart page for approximately 2 seconds, then switch to the fake login page to steal the user’s credentials. Without the domain changing, or any redirects occuring, the shopping cart disappears fast enough to potentially go unnoticed or be seen as a glitch, but it will fool any scanning technology that looks at the initial content returned and does not re-evaluate the page after the phishing payload is delivered. With traditional domain trust scanning, the domain will quickly be considered trustworthy, as there is nothing inherently suspicious about a shopping cart application hosting a shopping cart. The screenshot below represents the shopping cart page that is displayed for a few seconds, using the application samcart.
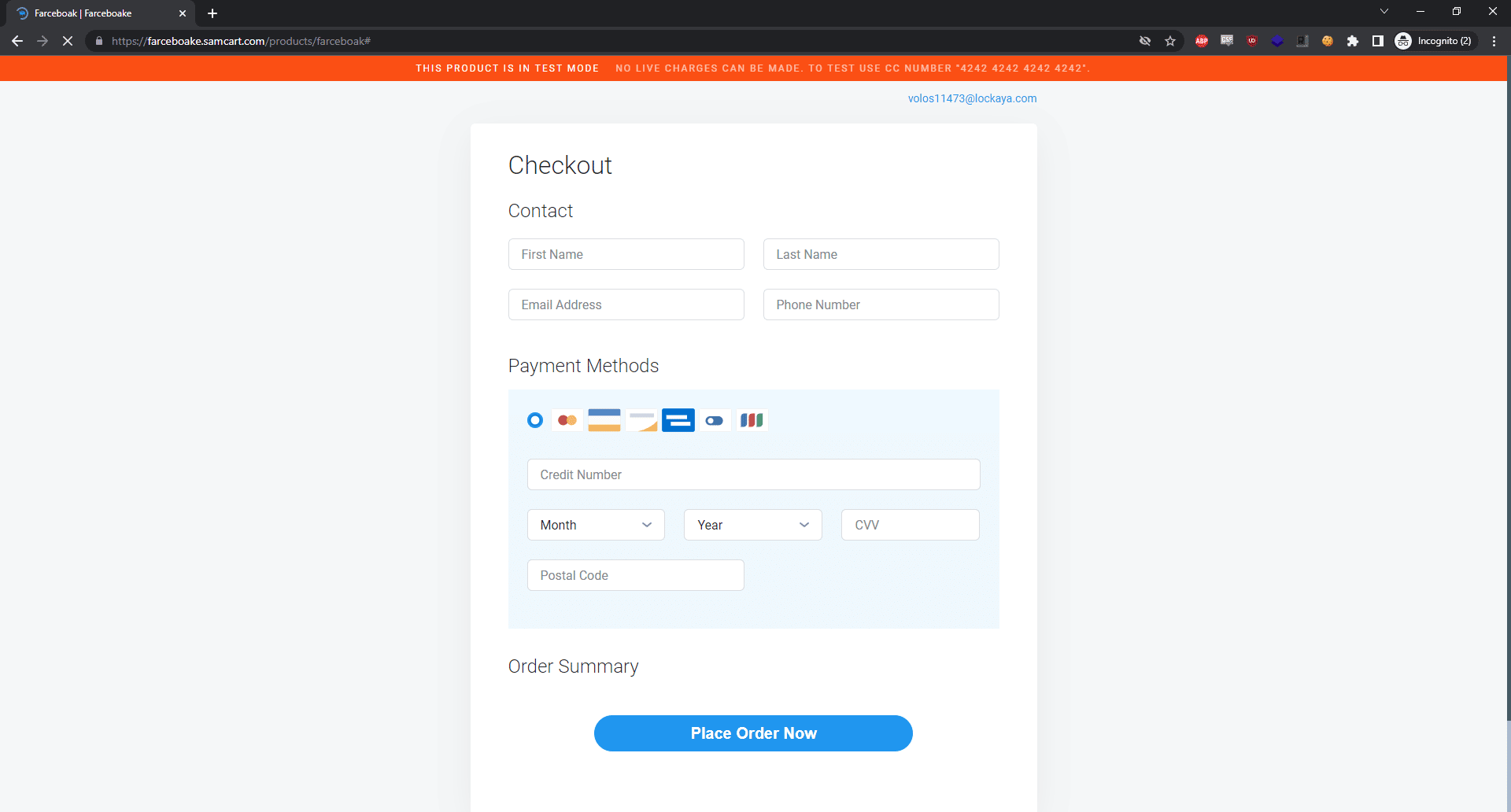
Our researchers first began seeing this technique being used with this campaign on June 9, 2022 and it has since been used in most of the new instances of the campaign that we have detected and stopped. A video demonstration of the technique in action can be viewed below.
As you can see, the shopping cart image is quickly shown to trick any phishing detection solution in place, after which the user is taken to the phishing page to enter their Facebook credentials for the malvertising campaign.
The Real Impact - Why Business Is Affected
Corporate security teams may read this and think, “why should I care about Facebook credentials?” Before completing that thought, it might be a wise idea to go through your corporate applications and check the settings for SSO providers. More and more business applications are leveraging SSO or requiring two-factor auth with an outside service, and Facebook is one of the leading third-party providers for authentication tokens. There are many business applications that permit Facebook to be used to authenticate, making it possible for an attacker to jump from a user’s home Facebook account directly into an application that may be hosting sensitive company data. Campaigns of this scale are almost certainly leading to compromise of corporate information systems, though we can’t know for sure which companies or systems are affected.
We will continue to monitor and publish our research on this large, evasive social media phishing campaign in the hope that we can help to prevent future instances of this type of campaign from taking place.
As in the previous story, PIXM would like to thank Nick Ascoli of Foretrace for his assistance in this investigation.
Contacts
Media Contact
Leslie Kesselring
Kesselring Communications for Pixm
leslie@kesscomm.com

Recent Comments