The beginning of April has seen continued targeting of corporate credentials via stealthy means and file share platforms as well as personal account phishing on work devices, including a marked increase in financial services and Netflix phishing campaigns, often including a tech support component. Here are a few examples and highlights.
Phishing URLs
kyschools[.]mgdinvests[.]com
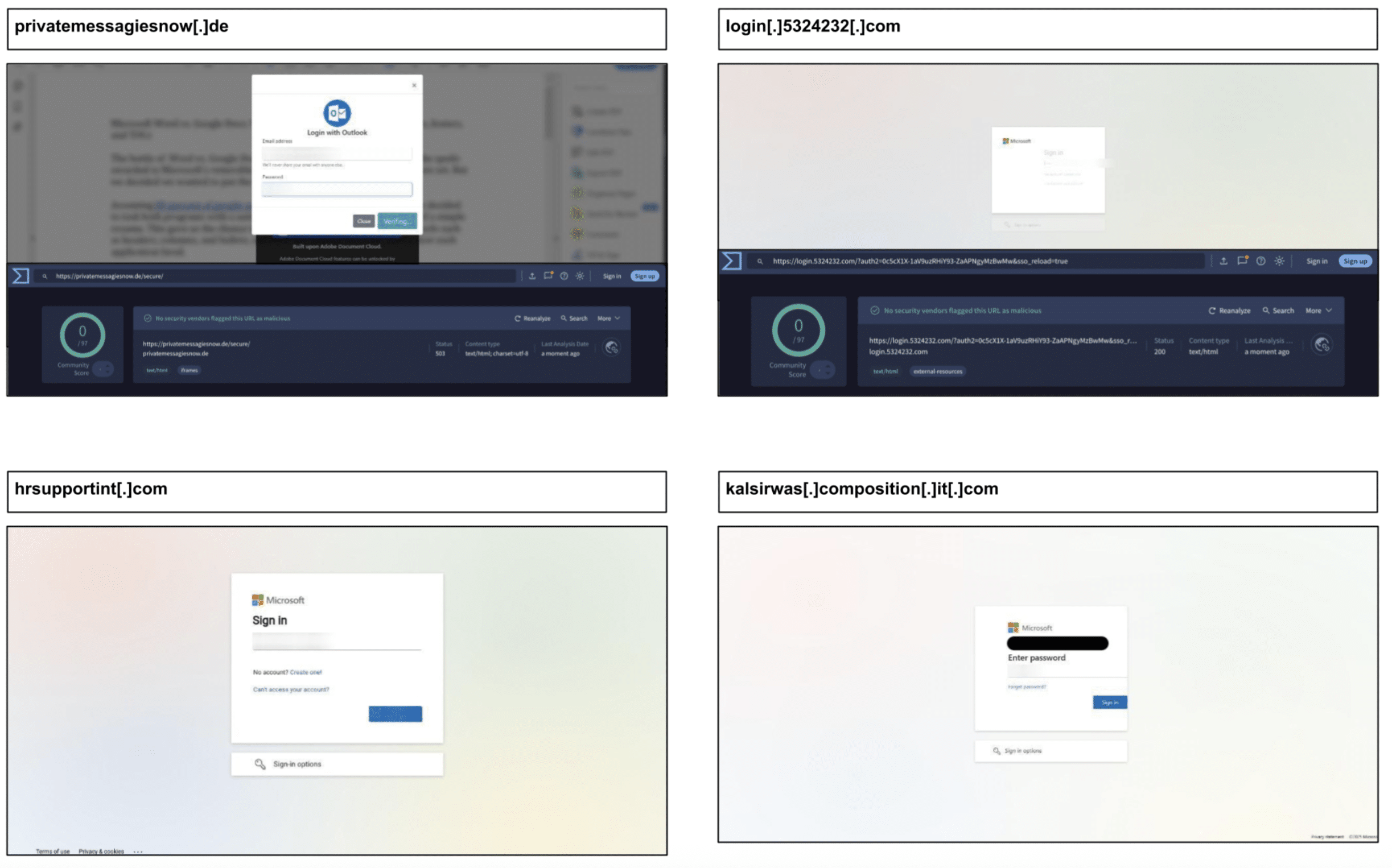
privatemessagiesnow[.]de/secure/
zentratech[.]online/services[.]php/
login[.]5324232[.]com
hrsupportint[.]com
alonglifewithparkinsons[.]com/service/3123eacc/54e5
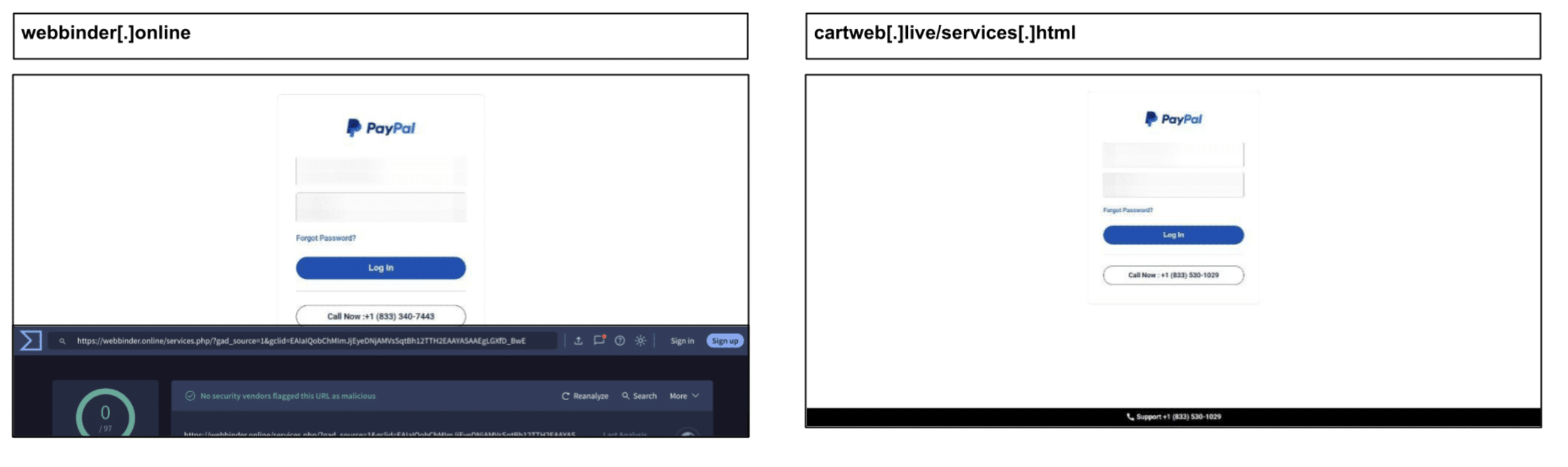
cartweb[.]live/services[.]html
heb6[.]ewetanign[.]ru
kalsirwas[.]composition[.]it[.]com
srhfree0w345-hgr[.]es/on/sd/
webbinder[.]online/services[.]php
Widespread Kentucky Phishing Campaigns
On April 2nd, 3rd, and 4th, the below Microsoft phishing link was clicked by 5 users across 3 organizations in Kentucky.
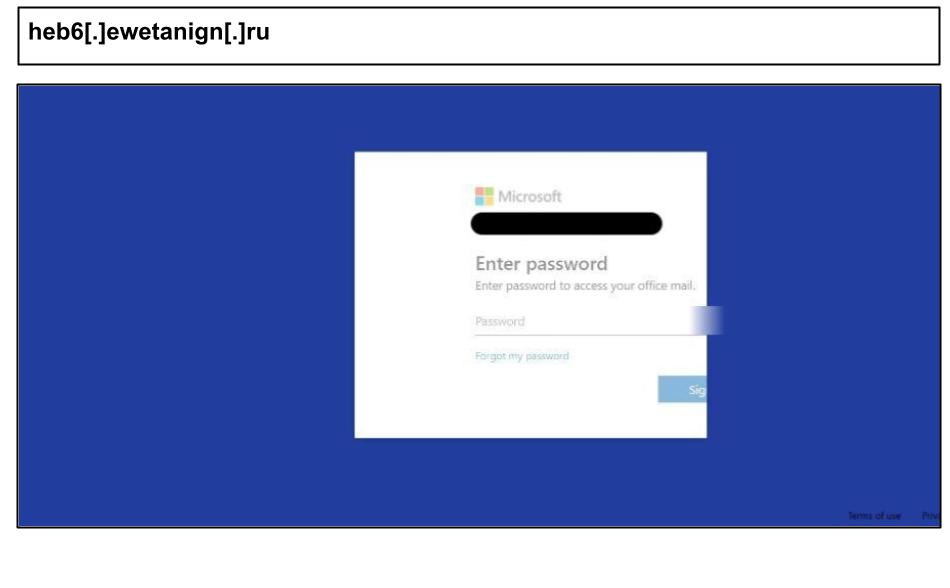
In addition to Microsoft, the page also impersonates Okta and GoDaddy, and also incorporates stealth redirect tools to legitimate sites depending on the client. For example, if the browser accessing the page is running in debug mode, the HTML redirects the site to homedpot.com. The URL itself was almost certainly generated by an algorithm, indicating it was part of a wider set of phishing attacks, was hosted on a Russian top level domain, and used path variables to target its users.
Another campaign targeted Kentucky school districts using subdomains matching real domains used by the public school system, like the below attack which was clicked on April 1st by a staff member.
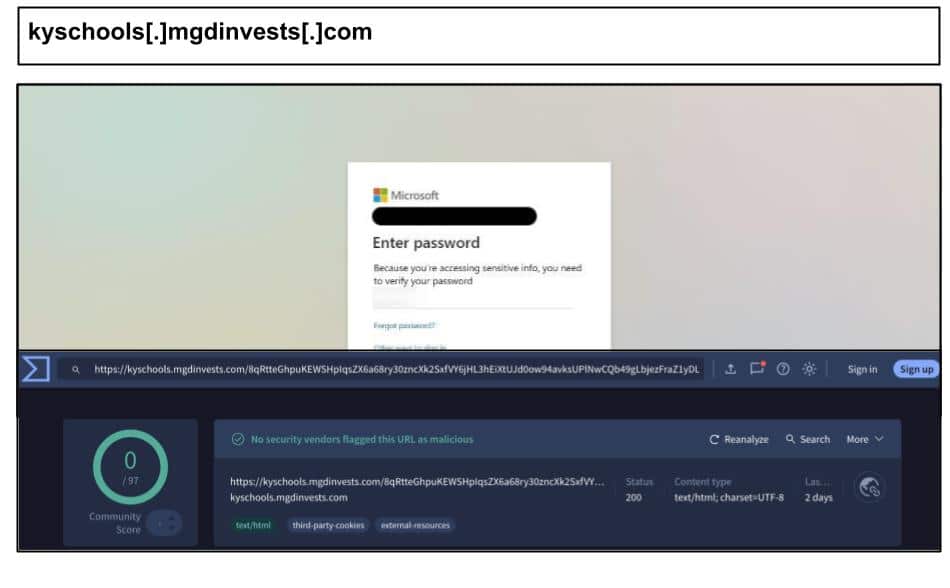
‘kyschools’ is a reference to the Kentucky public school system, which would normally use ‘.kyschools.us’ domains.
The same period saw sustained corporate credential phishing bypassing email protection and delivered through fileshares spread throughout Texas, Illinois and Georgia. Here are a few examples.
Customer Service Paypal Phishing
This period saw sustained Paypal phishing campaigns hitting users in Georgia, Texas, and Nevada. The below example was clicked by an employee at a Texas organization on April 9th.

Like others, it included a tech support component and tracking parameters suggesting possible abuse of ad networks to drive traffic and the use of cloaking or redirecting services to avoid detection by security scanners. Here are a couple of other similar examples.
Netflix Phishing
The period had a continued streak of stealth Netflix phishing, like the below example that was clicked by a staff member at a Georgia organization on April 4th.
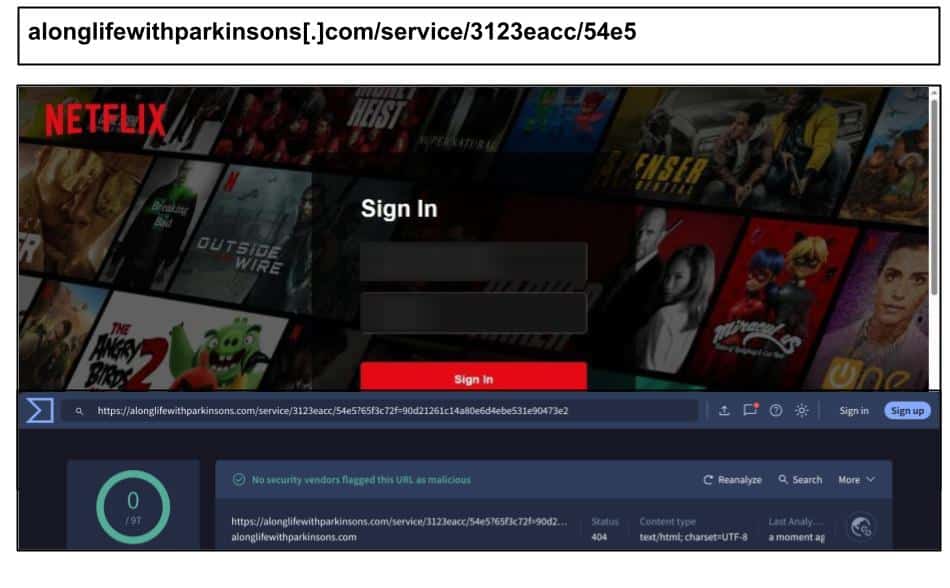
The domain hosting the attack is a legitimate site about the Parkinson’s disease community, which was likely compromised and hijacked. Here are a couple of others seen hitting users in Florida and Kentucky.

Some of these pages simulated a Cloudflare challenge, possibly to trick web crawlers into thinking the page is protected by a security provider.
Mitigations
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Educate users about phishing risks in file sharing applications outside email like Share Point and One Drive
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Educate users to find the valid support number for their financial service institution via Google and not to call the number provided on an unverified web page
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.

Recent Comments