Intro
It is rare that the identities of participants and ringleaders in criminal phishing schemes are uncovered. But in many cases, when untangling the web of a cyber criminal group (particularly with financially motivated e-crime actors), there are enough OSINT breadcrumbs left behind by a threat actor, on forums, in code, or elsewhere, to point investigators in the right direction.
In the case of PIXM’s investigation into a large scale Facebook credential harvesting campaign that has been active since Q4 2021, not only were those breadcrumbs very much available, but we uncovered a campaign whose scale has potentially impacted hundreds of millions of facebook users, and whose complexity offer insight into the evolving nature of phishing operations, especially from a technical perspective. This serves as a highlight of the challenges this evolving approach presents to traditional phishing site detection.
Technical Details
PIXM detected a fake facebook login portal that a user had attempted to visit in September of 2021. The volume of pages from this campaign would steadily rise, peaking in April and May of 2022. The image seen represents the structure of the landing page, which would remain almost completely unchanged until this very day, as the campaign continues to grow.
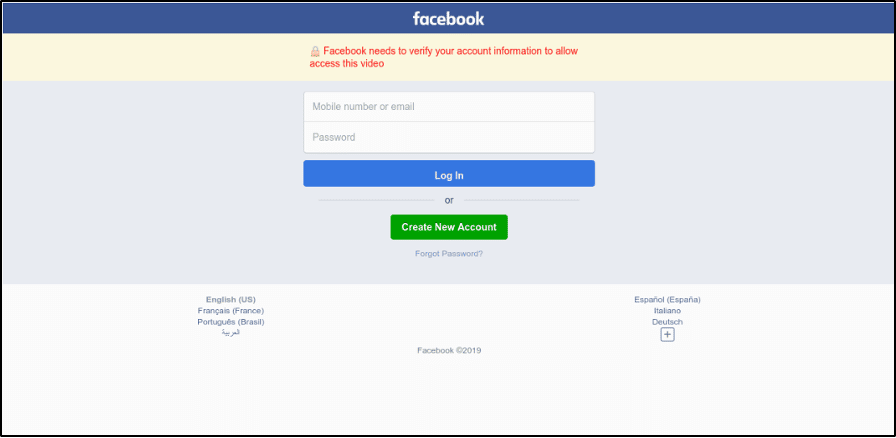
Upon inspecting the code associated with the website, PIXMs threat research team uncovered some interesting items:
- A reference to the actual server which is hosting the database server to collect users’ entered credentials. This always differed from the original URL the user visited, eventually landing on from a series of redirects.
- A link to a traffic monitoring application. We discovered the tracking metrics for this service can be viewed unauthenticated.This allowed us to not only view the threat actors traffic data for this landing page, but hundreds of other landing pages the actor had developed.
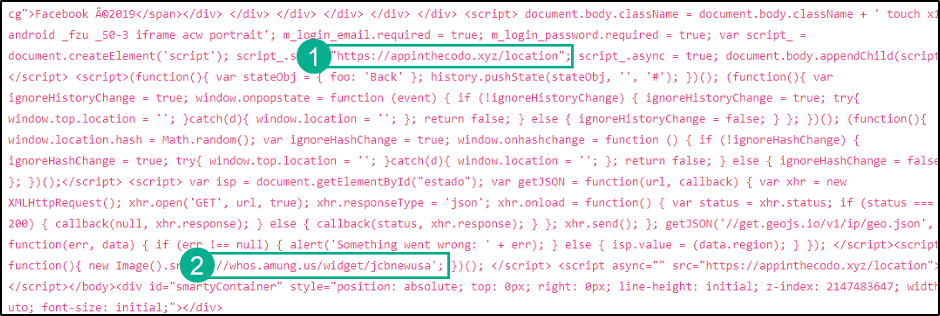
As the sites continued to pour in, there was only one observed change in the HTML on each page. The server name referenced in (1), and the username which would follow the traffic monitoring url in (2) i.e. //whos.amung.us/widget/*new username*
It appeared evident that these links originated from Facebook itself. That is, a users account would be compromised and, in a likely automated fashion, the threat actor would login to that account, and send out the link to the users friends via Facebook Messenger. Facebooks internal threat intelligence team is privy to these credential harvesting schemes, however this group employs a technique to circumvent their URLS from being blocked. This technique involves the use of completely legitimate app deployment services to be the first link in the redirect chain once the user has clicked the link. After the user has clicked, they will be redirected to the actual phishing page. But, in terms of what lands in facebook, its a link generated using a legitimate service that facebook could not outright block without blocking legitimate apps and links as well.
This threat actor uses popular services like glitch.me, famous.co, amaze.co, funnel-preview.com, among others. These websites are used to deploy, and generate URLs, for complete legitimate apps, but are also regularly used by threat actors due to their ease of rapid deployment. While the threat actor was using my.famous.co, for example, the link to their site would simply be ‘my.famous.co/*unique ID*. Once one of them was found and blocked, it was trivial (and based on the speed we observed, likely automated) to spin up a new link using the same service, with a new unique ID. We would often observe several used in a day, per service. This is illustrated below in a screenshot of my.famous.co domains (All from the same campaign) submitted to URLscan.io.
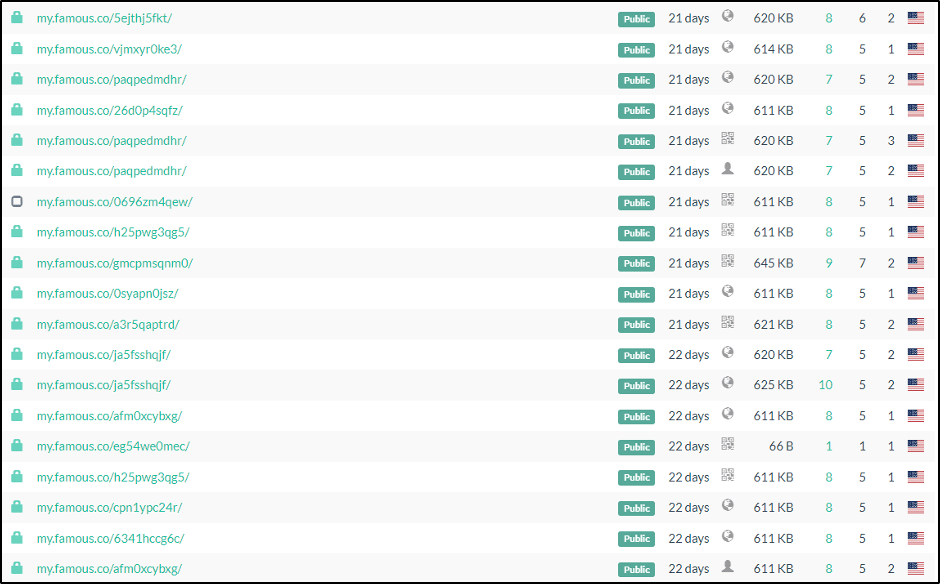
The use of these services allows the threat actors links to remain undetected and unblocked by Facebook Messenger (and by domain reputation services) for long periods of time. This approach has yielded enormous success for the threat actor.
Campaign Scale
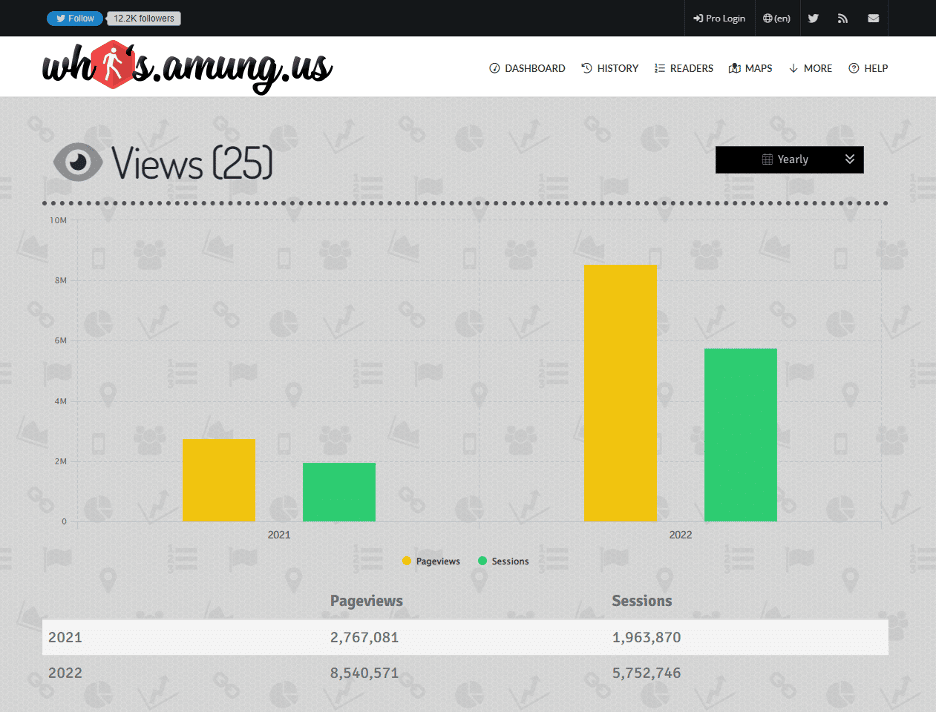
To quantify the success of this campaign so far, we look to the traffic monitoring application the threat actor has been leveraging – whos.amung.us. To view the statistics of one of these links, we search the HTML for a reference to a whos.amung.us username, and discovered we could view that users dashboard by simply navigating to whos.amung.us/stats/username.
When we visit this URL using one of the threat actors usernames, we arrive at this page. It shows us active sessions under ‘Readers’ on websites using this tracking code, and the actual URLs those sessions are on. To view statistics, we browse to the Views page, under the More dropdown.
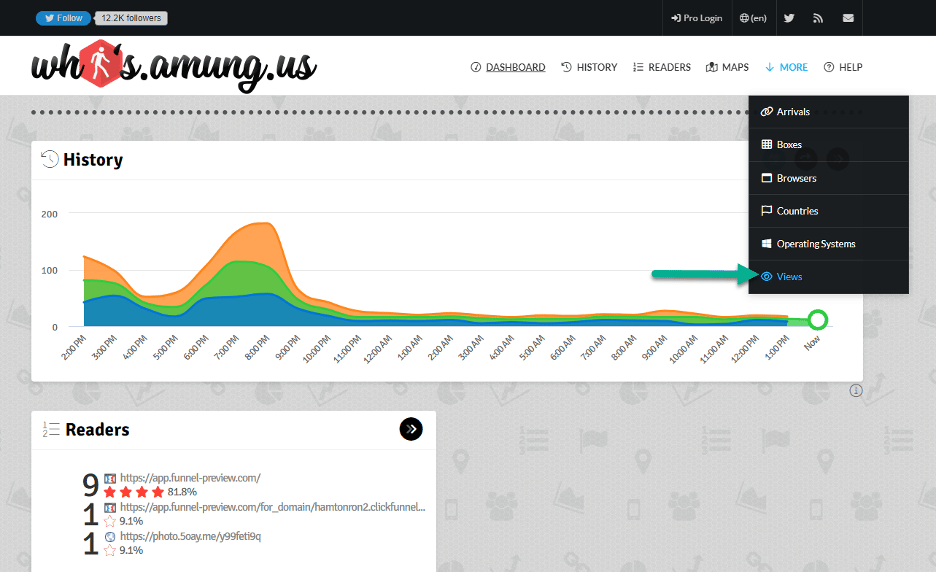
While viewing the Yearly Views page, we see 2.7 million users visited one of their pages in 2021, and around 8.5 million so far in 2022. This represents tremendous growth in the campaign from 2021 to 2022.
So far, we have identified roughly 400 unique usernames, all connected to different facebook phishing landing pages, but all associated with the same campaign. When taking an average from just 17 random usernames, we see each unique username receiving 985,228 pageviews so far. (Some of these usernames are still being used – live stats can be viewed by navigating to whos.amung.us/stats/[username]).
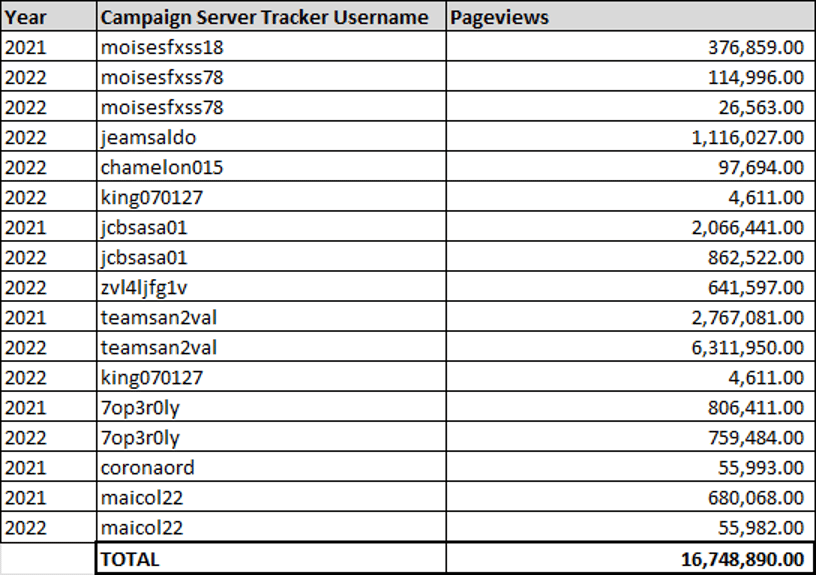
When extrapolated over the 400 unique usernames we identified, that’s 399,017,673 total sessions, and rising fast. We estimate that the 400 usernames identified so far, and all of their unique phishing pages, only represent a fraction of this campaign.
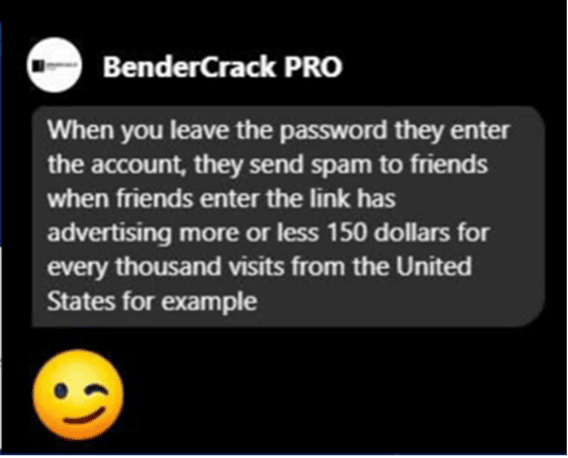
When an OWASP Researcher reached out to the threat actor while researching this campaign as it started in 2021, the threat actor claimed to make ~$150 for every thousand visits from the United States. With an estimated total of 399,017,673, that would put this threat actors projected revenue at ~ $59M from Q4 2021 to present. We think its safe to assume this threat actor is, well, probably exaggerating quite a bit, but the revenue is still likely staggering considering the size of the campaign.
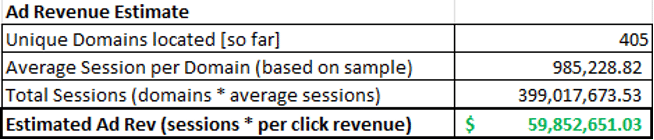
This revenue is generated from a combination of ad tracking tools on the landing pages, and the redirects after a user enters their credentials on the phishing page. These pages will typically route to a malvertising or advertising page prompting additional interaction from the user, which the threat actor collects referral revenue from.
Identifying the Threat Actor
Now – time to make bread from the attackers’ breadcrumbs. In the series of redirects for these landing pages, on virtually every site we encountered from this campaign, the same code snippet can be found (this remains true on sites found on the same day of this blogs publication).
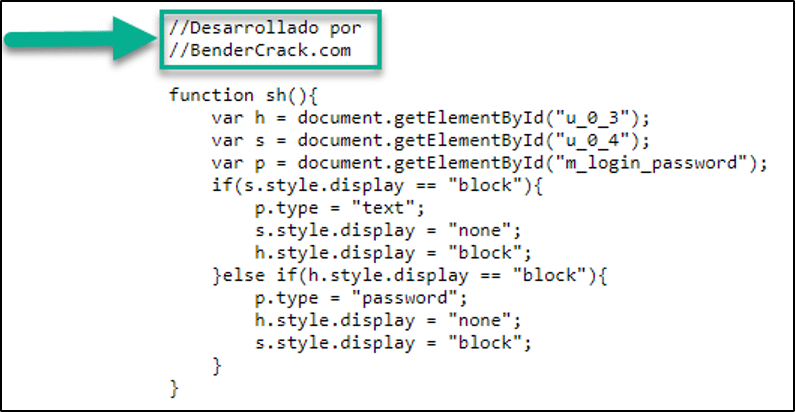
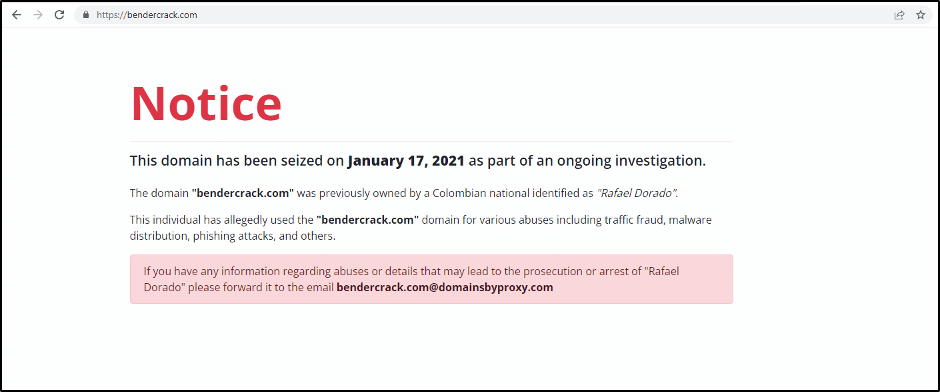
When translated from spanish to english, this reads “Developed by Bendercrack.com”. When visiting BenderCrack.com today, the site displays the following message:
When viewing archived copies of the BenderCrack site – the following phone number can be seen, referenced as contact information for the sites owner.
While performing a reverse whois lookup on that phone number, we find it associated with several websites, whos associated registration contact email is ‘rafaeldorado001@gmail.com’.
While looking at other sites registered with this email address, or referencing it as contact information, we were able to locate the threat actors legitimate web development businesses and office locations in Colombia, and several old sites of their other offerings including facebook like bots, hacking services, and other illicit web business, plus various aliases the threat actor uses online (including the usernames developerdorado and hackerasueldo).
More detailed points of identity attribution were collected, but will not be shared in this blog. That information has been passed to the Colombian Police and INTERPOL.
Previous Research
In early 2021, this campaign was noticed by Mantas Sasnausaks, an OWASP researcher at the time. Mantas published a report on their findings, and published an article to cybernews.com. The campaign appeared to slow down for several months after these reports, but then returned again in late 2021, with a scale and private server count eclipsing that which was previously uncovered, and now leveraging a litany of legitimate web application hosting providers. As we have monitored the threat actor spinning up new domains and servers, we see a rotation between different providers, and we observe them regularly testing out new providers before actually hosting phishing content with them.
Why Does This Matter
The rise in use of legitimate services to circumvent URL blocking by traditional domain reputation analysis solutions has proven enormously successful for threat actors, and as a trend, continues to be on the rise. In many cases, testing these URLs in domain analysis tools, would yield no results indicating the page is suspicious or should be blocked. A majority of security suites which analyze domains for suspicious properties would allow a connection to these domains to proceed, as several key metrics of trustworthiness would be satisfied by the parent domain hosting the site (in every case, a completely legitimate web service). As long as these domains remain undetected by use of legitimate services, these phishing tactics will continue to flourish.
PIXM's Role In This Investigation
PIXM first detected phishing attempts against our customers in early 2022. While many of the phishing pages were not known or available in any threat intelligence feeds at the time, and had no obvious connection, PIXM’s real-time computer vision technology was able to detect them and prevent our customers from having their credentials stolen.
During routine analysis, we discovered the connection between the pages using PIXM’s deep html analysis feature, which enabled us to view and analyze the underlying code on the pages after they were flagged as phishing. This led to the ensuing investigation, which was led by PIXM’s threat research team with assistance from Nick Ascoli, CEO of PIXM partner ForeTrace.
If you’d like to learn more about PIXM, please reach out to us at sales@pixmsecurity.com or request a demo today.
Contacts
Media Contact
Leslie Kesselring
Kesselring Communications for Pixm
leslie@kesscomm.com

Recent Comments