Overview
December has continued to see targeted spearphish involving compromised mailboxes across Texas and Kentucky, as well as a massive surge in USPS phishing around the holidays. Below are some examples and highlights.
Phishing URLs
Here is a list of examples of phishing websites that we discovered that we recommend you update your threat intelligence with these URLs.
dchbxcsq[.]courtcloudservices[.]com/Tv0Kj/
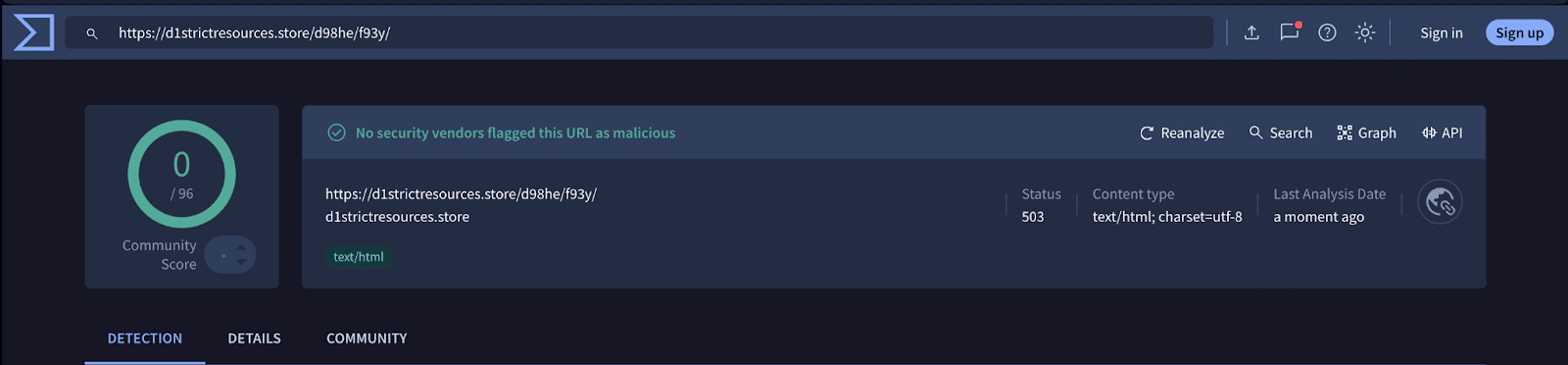
d1strictresources[.]store/d98he/f93y
resedaclinicaestetica[.]com[.]br/oned/index[.]html
summary-netfilx[.]renew-mysubscription[.]billing-center[.]netfilx[.]com[.]tamiresribas[.]com[.]br
usps[.]com-trackxgb[.]top/us
usps[.]com-parcelplxh[.]vip/i/
usps[.]com-trackcexk[.]top/
usps[.]com-postaasxz[.]top/us
Family Business Email Compromise
On December 10, a staff member at a Texas organization clicked a spearphish link targeting their Microsoft credentials in a PDF file.

In this instance, the phishing email was sent by the personal Gmail account of the staff member’s spouse, who had been compromised. The phishing email contained a link to a password protected PDF stored in Google Drive, which, upon being unlocked, contained a link to a Microsoft credential harvester. This is hard to detect because it involves both a trusted sender address and a password protected file that contains the phishing link.
Another spearphish was clicked by three staff members at a Kentucky organization on Dec 9th.
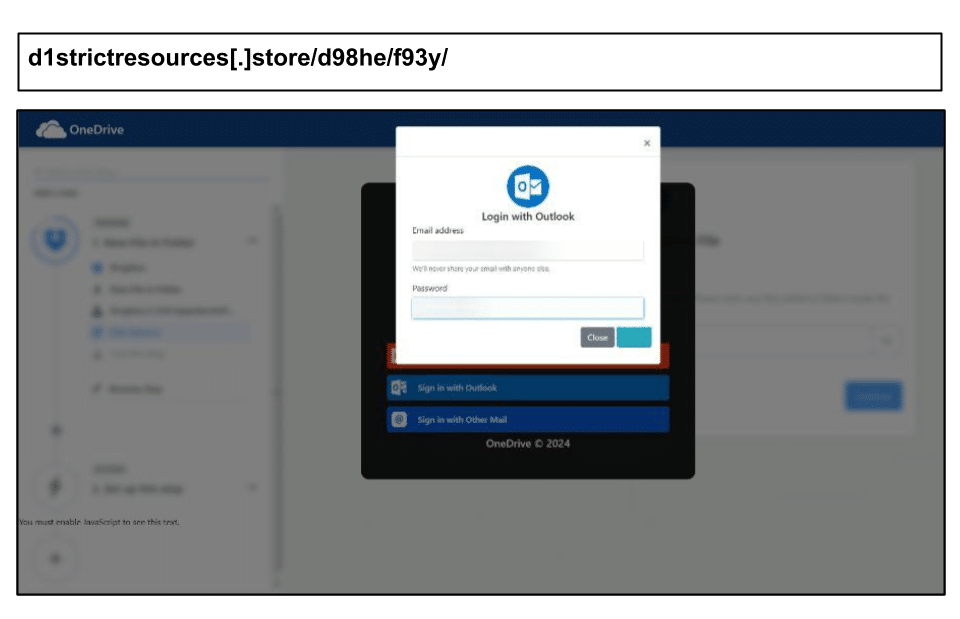
This was delivered through a OneDrive file share outside the scope of normal email protection. Even seven days after it was detected by PhishID, it remained undiscovered by the entire VirusTotal community.
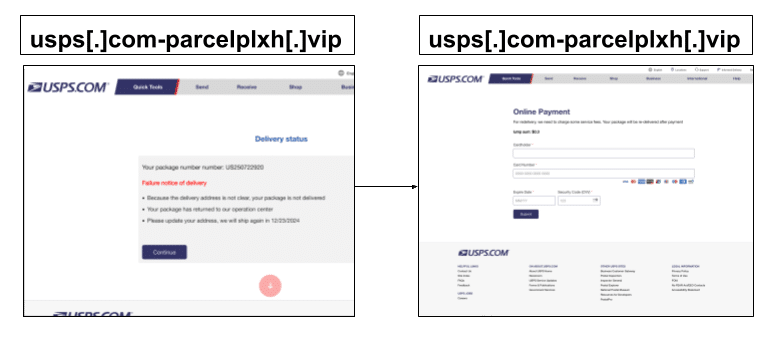
Credit Card UPS Phishing
Leading up to the holidays, PhishID picked up a surge of UPS phishing attacks clicked by staff members across districts in Washington, Kentucky, and Idaho.
To highlight one instance, a UPS phishing link leads to a page that says that a package has been returned because the delivery address is not clear. In order to have the package delivered by Dec 23rd, the page says, the user must update their address.
Upon clicking ‘Continue’, the user is directed to an address form, and is then further directed to an online payment form in order to pay for a minor supposed delivery fee. Numerous links on the phishing page actually linked to the legitimate UPS website. Scams like this leverage anxiety that packages arrive before Christmas. They are further difficult to detect by concealing credit card solicitation until the user has clicked through multiple forms.
Suggested Actions
- Add the specified domains to your block lists.
- Focus awareness efforts on high-risk credentials.
- Educate users to exercise caution when opening links even when they are delivered from family members and involve password protected files.
- Educate users that phishing in their personal email can pose serious risks.
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
threats@pixmsecurity.com

Recent Comments