
The end of May and first week of June 2025 saw a sharp uptick in zero-day phishing campaigns targeting corporate login credentials, with additional campaigns impersonating Amazon and even U.S. government login services (ID.me for IRS). Threat actors employed sophisticated evasive techniques – from multi-layer code encryption and clipboard hijacking to spoofing Microsoft’s own telemetry tools – allowing many of these credential harvesters to slip past traditional security filters. Here are some examples and highlights.
Phishing URLs
py3zy[.]rzcpsgsgtl[.]ru
4qedv[.]nubelith[.]es
manageapps[.]rkv[.]yeo[.]mybluehost[.]me
alcornic[.]com
bayviewsbuildermd[.]com
y2h1ux[.]de
oug1e[.]dzdyf[.]es
managesecure[.]log-in[.]information-reactivate-statement[.]prime[.]vmr[.]jtu[.]mybluehost[.]me
live.messages[.]landscapeeconomics[.]com
dinerpro[.]info
ID.me / IRS Account Phish
On June 4th, a Kentucky user clicked a phishing page impersonating an ID.me government login for IRS verification.
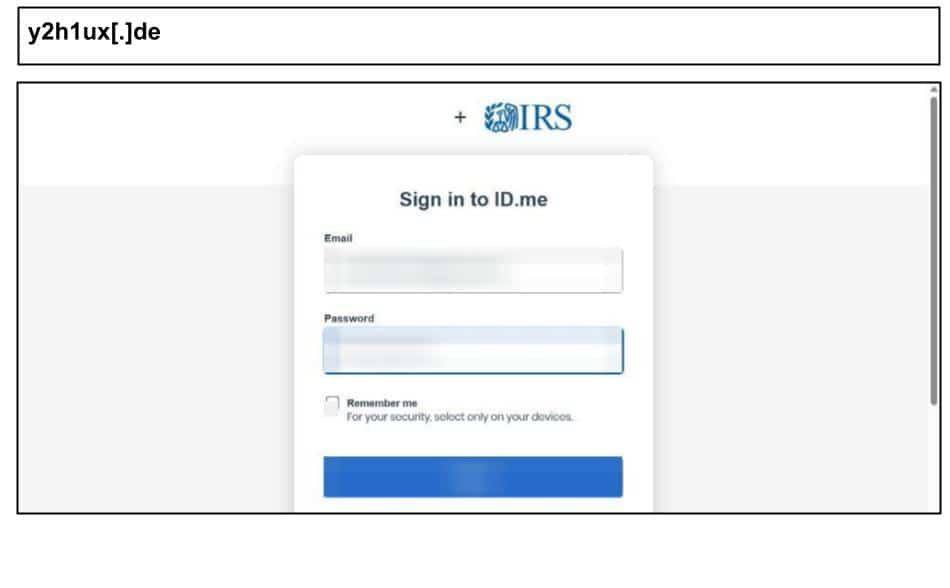
Similar reported phishing attacks are delivered via emails prompting users to “verify now” to avoid losing access to IRS services. The attack not only asks for ID.me credentials but also additional personal data like Social Security Number, date of birth, and even IRS specific identifiers like CAF and PTIN numbers. Had the attack been successful, the attacker could commit identity theft, file fraudulent tax returns, or use the stolen data for broader attacks involving MFA bypass.
Corporate Credential Phishing
The period also saw an uptick in targeting of corporate Microsoft credentials. On May 27th, a Texas user clicked the below Microsoft spearphish.
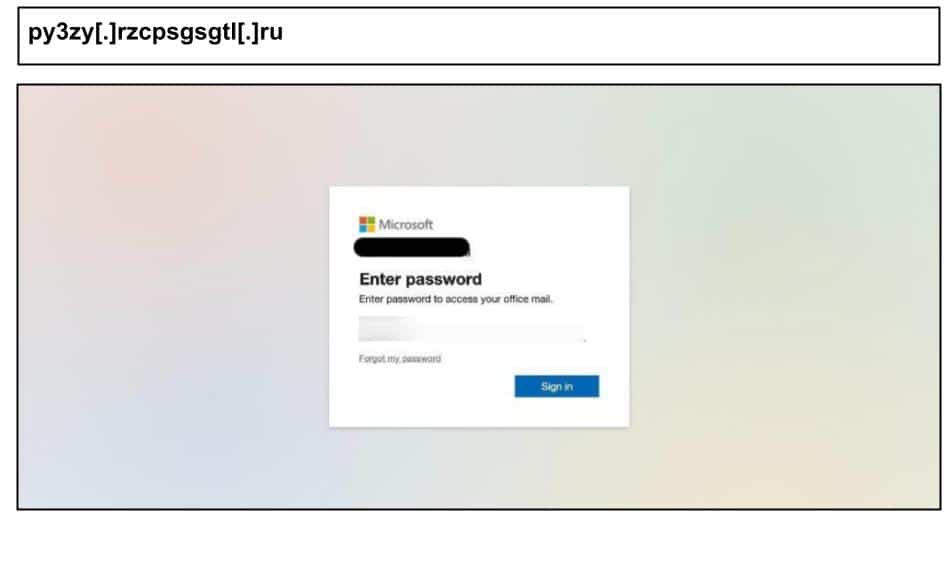
The attacker used a layered decryption chain to obfuscate the phishing content from static analysis. On June 2, another Texas user clicked the below phishing attack hosted on a domain likely generated by the same algorithm as the May 27th incident.
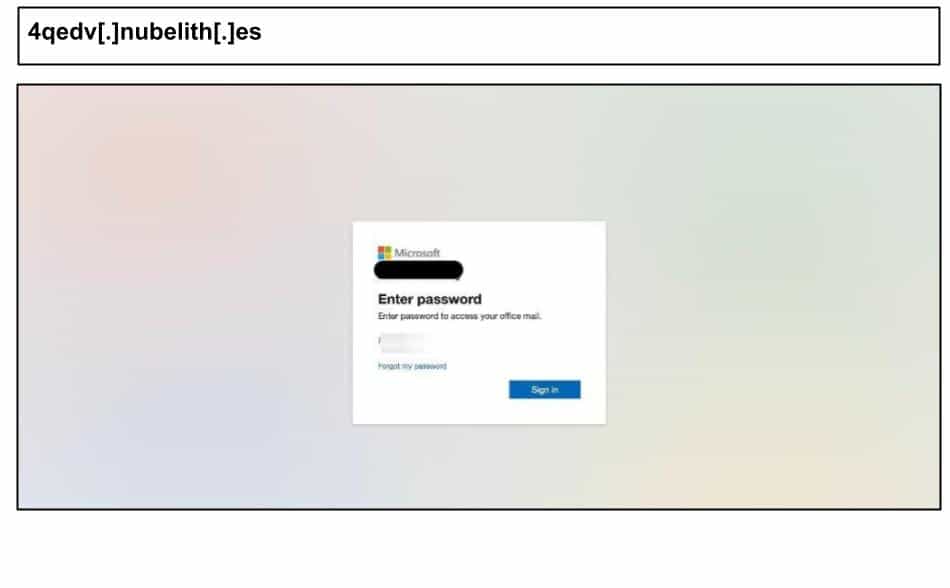
Like the May 27th incident, it used multiple layers of decryption and additionally used clipboard hijacking to make analysis harder. This was clicked by two Texas users on the same day.
On June 2nd, a Kentucky user clicked the below spearphish that perfectly mimicked Microsoft’s OAuth flow in the URL.
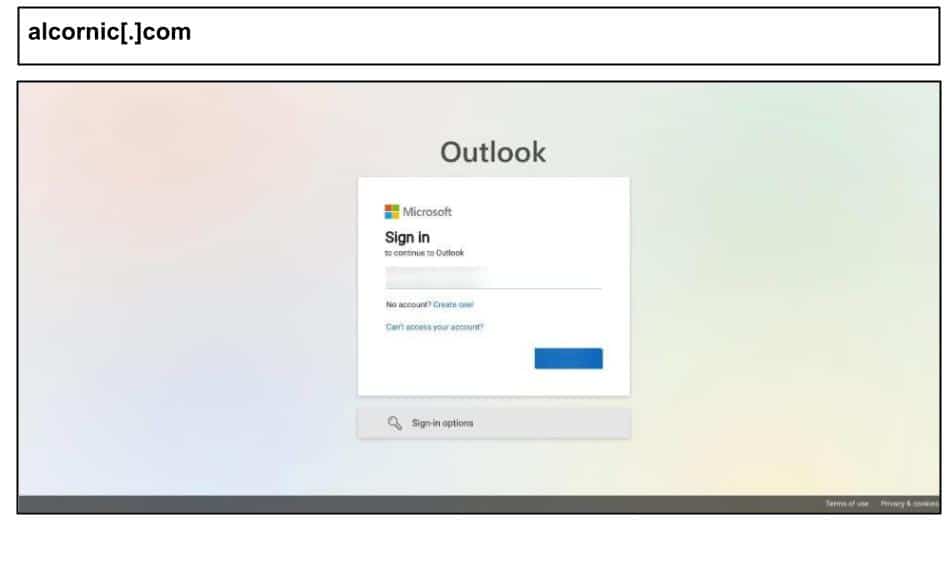
The HTML includes a large amount of Microsoft-branded meta data to obscure the core phishing logic. The attack was clicked by four different users on June 2nd and 3rd at multiple Kentucky organizations.
The same day, another three Kentucky users clicked the below spearphish that included spoofing of Microsoft’s internal telemetry reporting tool (Watson).
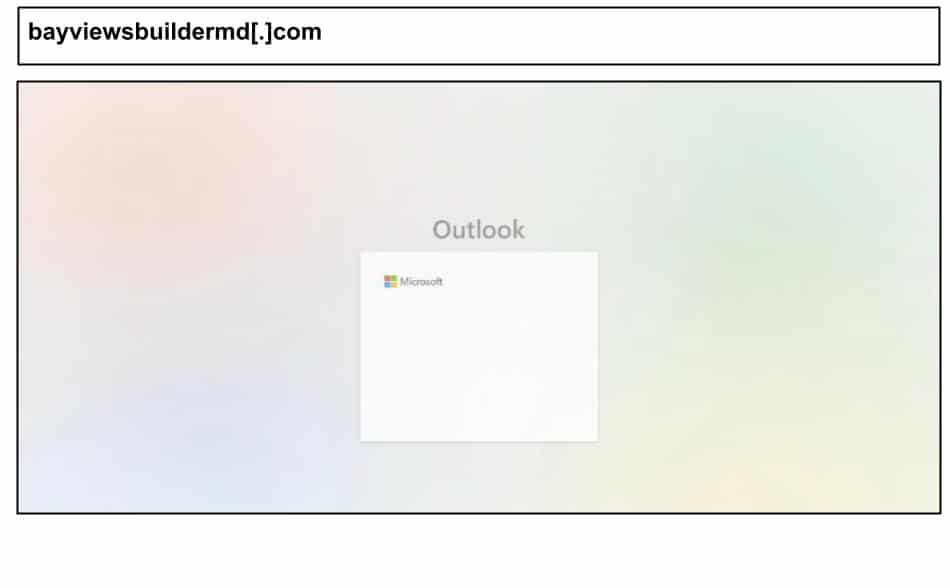
On June 4th, a user in Washington clicked a Microsoft spearphish that was hosted on a compromised domain that was unwittingly hosting a phishing attack, making it difficult to detect by reputational tools.
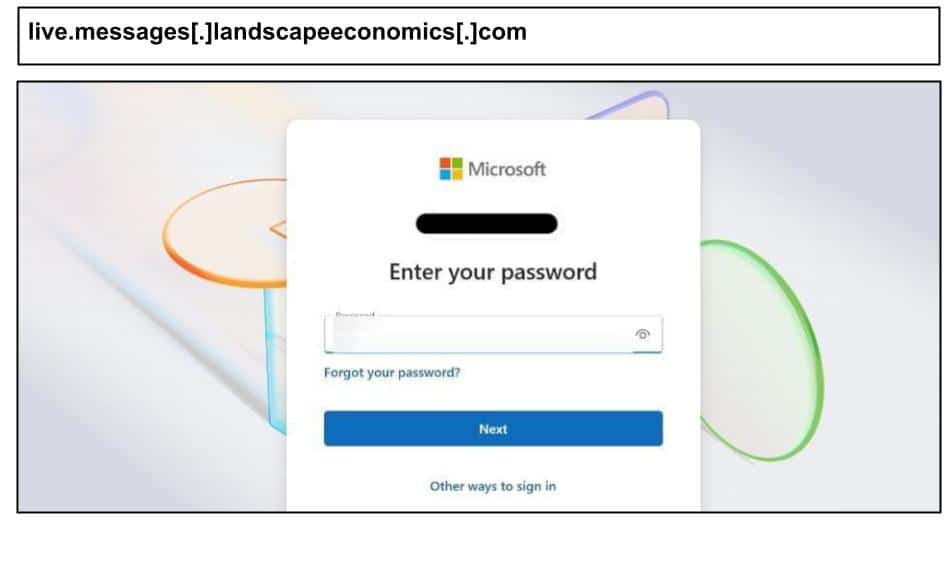
The full URL mimics Microsoft’s OAuth 2.0 structure. The phishing attack also utilizes device fingerprinting for future targeting.
Amazon and Multi-brand Phishing
The same period saw an uptick of Amazon phishing targeting personal user accounts on work devices that were hosted on the same mybluehost[.]me domain noted in earlier reports. Below are two examples that were clicked by users in Ohio and Kentucky.

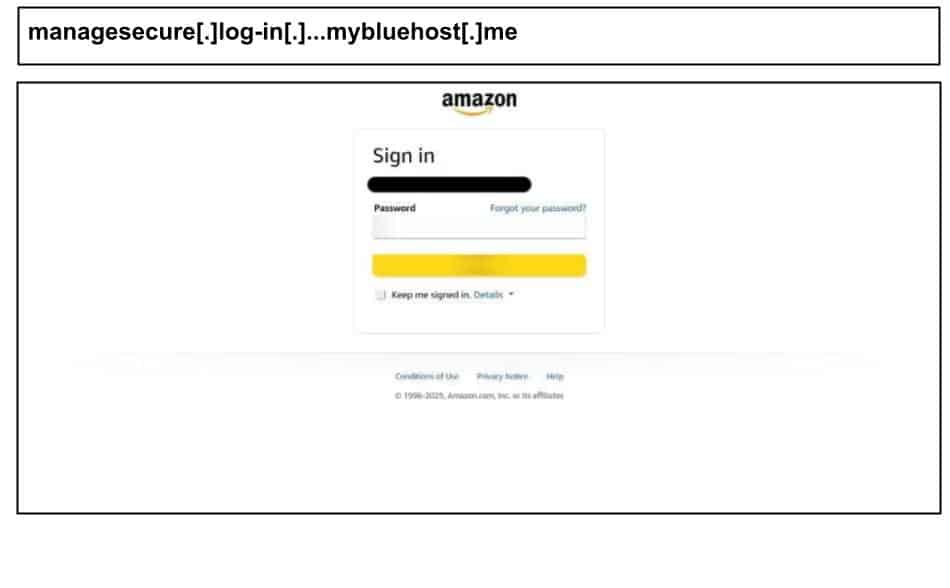
The last example full URL includes the keywords like “reactivate” and “Prime” strongly suggests an Amazon Prime membership scam – likely a phony alert that a Prime account was suspended or needed updating.
On May 31st, a Kentucky user opened a multi-brand phishing attack via an Adobe fileshare.
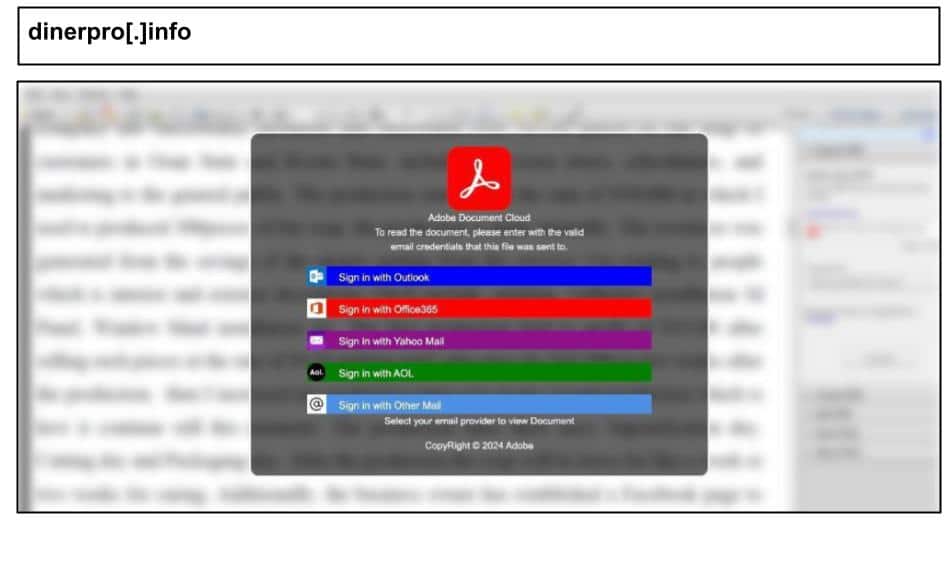
This attack targeted numerous credential type and included a MFA phishing stage after password credentials were harvested.
Mitigations
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Educate users about phishing risks in file sharing applications outside email like Adobe
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
- Protect your users from the next wave of zero day phishing attacks and schedule a demo.
threatresearch@pixmsecurity.com

Recent Comments