Overview
The last two weeks have seen an uptick in spearphish targeting corporate users on their personal accounts as well as a burst of Netflix phishing activity. Here are some examples and highlights.
Before we dive in, here is a list of examples of phishing websites that we discovered and we recommend you update your threat intelligence with these URLs.
Phishing URLs
hebelex[.]com/
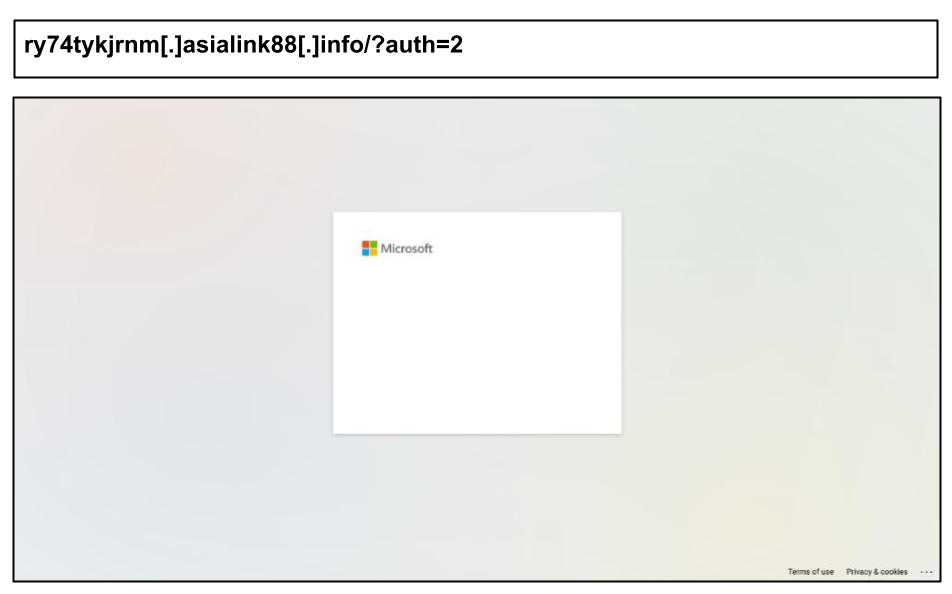
ry74tykjrnm[.]asialink88[.]info
taxliencode[.]constructappsolution[.]com
2ndlinksffice[.]appforconstruction[.]com/
onlinery[.]norterc[.]com/
signin[.]neflix[.]payment-reminders.144-126-136-207[.]cprapid[.]com
payments[.]oauth-netflix[.]updateverification[.]50-6-173-246[.]cprapid[.]com
signin-netflixpaymentsupdates[.]50-6-172-50[.]cprapid[.]com
Personal Email Delivery
On November 25th, a staff member at a California organization clicked on a spearphish targeting their Microsoft credentials. While the hacker was targeting their professional email password, the end user confirmed that they clicked the phishing link in their personal email.
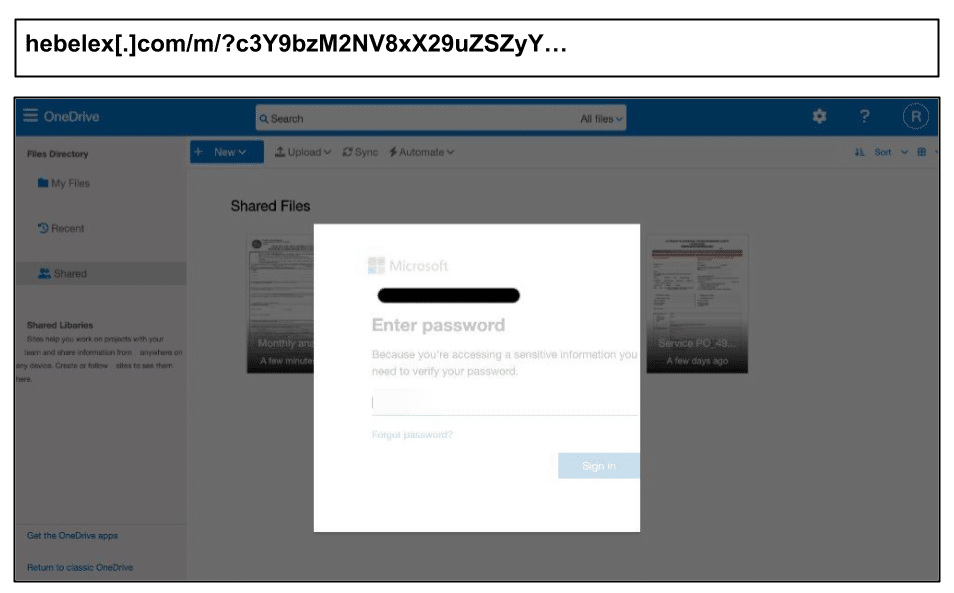
Hackers know that corporate email is better defended than personal email. Targeting users via their personal email often, therefore, presents a path of less resistance.
Lateral Phishing
On Thanksgiving day, a staff member at a Kentucky organization opened the below spearphish. It was sent from a valid email address from a known business associate at a local Home Builders Association.
The previous day, an executive at the Home Builders Association had their own corporate email compromised. Leveraging the trusted communications with their contact, the hacker sent an email to the targeted user via the compromised account.
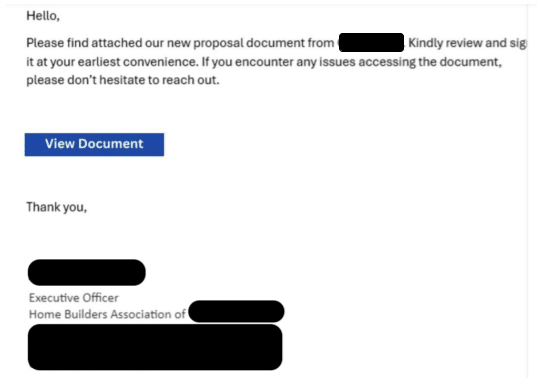
The email contained a View Document call to action, referencing a proposal that was likely anticipated by the recipient. The full email included the sender’s signature and headshot photo of the sender.
Netflix Surge
During the same period, we saw a large surge in Netflix phishing attacks being clicked in districts across Georgia, Texas, and Washington.

Numerous subdomains were detected like the above that use disposable hosting services so that they only stay active for a short period. The phishing attack further redirects security sandboxes to a legitimate Netflix help page. Most of the URLs reference billing or payment.
Suggested Actions
- Add the specified domains to your block lists.
- Focus awareness efforts on high-risk credentials.
- Educate users that phishing in their personal email can pose serious risks.
- Educate users to exercise caution when opening links even when they are delivered from trusted associate email addresses.
- Deploy the PIXM extension to protect your users from the next wave of zero day phishing attacks
If you would like a demo of Pixm to learn more about our AI technology and how we can help protect your customers, sign up here.
Questions or Feedback
PIXM Threat Research Team
threats@pixmsecurity.com

Recent Comments