
Phishing campaigns hosted on Backblaze infrastructure seen earlier in the September substantially ratchetted up in the second half, complete with credential exfiltration through Telegram and lures referencing purchase orders. Other widespread phishing campaigns that hit half a dozen organizations during this period used Attack in the Middle (AiTM) tools to exfiltrate two factor codes and session tokens in real time as users log in. We also saw sustained uptick in Microsoft scam scareware and phishing attacks targeting personal accounts like American Express and Netflix. Here are some examples and highlights.
tronklamnsj5rdf4[.]z13[.]web[.]core[.]windows[.]net
quinoa-sc2ddream[.]nagaisti[.]sa[.]com
secure[.]formloaders[.]com
login[.]beckleyrsvs[.]com
ferlo[.]psitesinternal[.]com
fdbn35fdhn[.]z13[.]web[.]core[.]windows[.]net/win[.]html
ghch78hjvhj[.]z13[.]web[.]core[.]windows[.]net/win[.]html
instantlyper[.]com
organizationbush[.]shop
8e3138d0-2704-45a8-a76f-a0748981346d-00-2e8qjjpf3umir[.]janeway[.]replit[.]dev
comejoinus[.]de/beepoint/AcrobatN/
globalconfidentialprobook[.]us-southeast-1[.]linodeobjects[.]com
f005[.]backblazeb2[.]com
Within 24 hours on September 23, phishing attacks hosted on Backblaze domain were clicked by 10 users across half a dozen organizations in Kentucky and Minnesota.
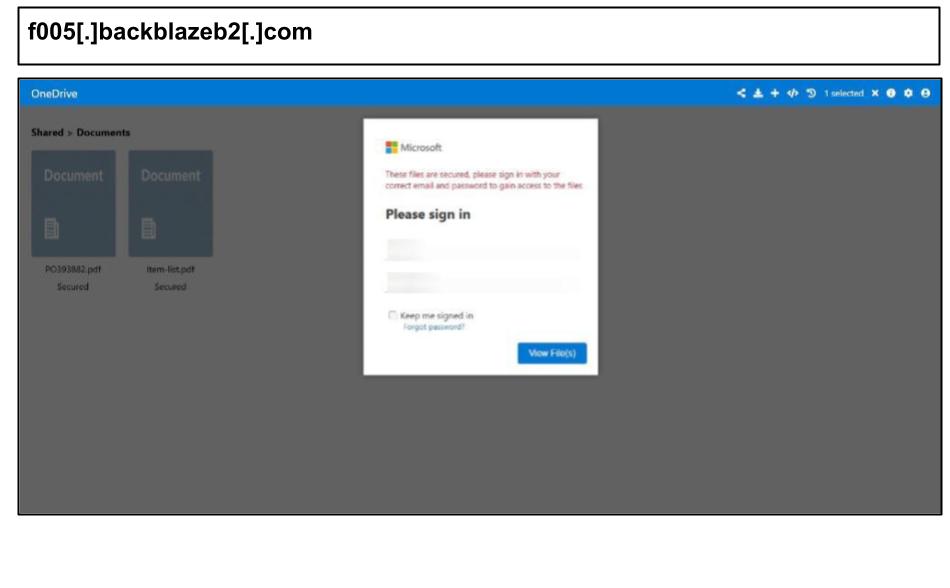
Similar to those mentioned in the last report, these exfiltrated credentials on Telegram’s Bot API and leverage third party infrastructure for reputation and TLS. The lure references a shared file via OneDrive and the page itself references a PO order, likely targeting procurement personnel.
The campaign made use of a cluster of URLs hosted on the same domain, for example:
f005[.]backblazeb2[.]com/file/soooodheeeded/onedr-updated[.]html
f005[.]backblazeb2[.]com/file/asssrrrruuueeee/onedr-updated[.]html
…
Other phishing attacks during this period used legitimate third party storage. On September 19, a technical director at a North Carolina organization clicked the below Microsoft phishing page.

Similar to the Backblaze example, this page is hosted on another cloud storage service, Linode Object Storage, again to leverage its reputation and TLS to bypass domain reputation filters. The page also has logic to detect headless tools and send them to a blank page, so that the page can avoid detection.
Another widespread campaign was first detected on September 16th, when a staff member at a Kentucky organization clicked the below Microsoft spear phish.

The page made use of Attack in the Middle (AiTM) phishing kits that relay the session to Microsoft while harvesting credentials and session cookies for MFA bypass. More sophisticated than most commodity AiTM phishing kits, this forcibly injects code into all JS set cookies that directly counters newer Chrome/Edge/Safari defenses against third-party cookies. Altogether, this phishing attack was clicked by 9 users in less than a day across 5 organizations.
It also makes use of a suite of subdomains to coordinate the attack across larger scale infrastructure: newnewdomnew*[.]beckleyrsvs[.]com
The same period saw a major uptick in general Microsoft spear phish and scareware campaigns. On September 15, a staff member at a Minnesota organization clicked the below Microsoft phishing attack.

A classic tech support scam, this page features a phone based scam, audio beeps, browser locks and other attention hacks to prod the user into taking action and calling the number. The page personalizes the messaging to the device’s region, eg. “Your device has been blocked by the state of ___”.
The same day, a principal at an organization in Kentucky clicked on the below Microsoft spear phish.

The page makes use of a long loader to placate the visitor while it acquires detailed device information both to better target the user and to evade detection in the event it is being scanned by a security tool.
On September 16, a staff member at another Kentucky organization clicked the below Microsoft phishing page.

The page references a larger group of subdomains of *.formloaders.com, likely as part of a phishing kit generating disposable instances to evade domain blacklisting and reputation-based blocking.
50b8883cece74335ad4ed2c0d7e5fcef.formloaders.com, 7fbf392b40364463bd1f4fcb152691ed.formloaders.com,
…
It further makes use of hidden scripts to automatically exfiltrate credentials before the user even clicks the submit button.
On September 17, an employee at yet another Kentucky organization clicked the below Microsoft spear phish.

The URL uses tracking tokens for each recipient, and the page itself has the target’s email pre-filled. The page redirects to the legitimate outlook.office.com after credentials are submitted, a common technique to avoid immediate suspicion.
The same day, an admin at the same organization clicked the below Microsoft scam.

This scareware page used aggressive browser lock behavior, including right click and the keyboard fully disabled, with special handling to block F5 and Esc. It also used mainstream analytics engines like Google Analytics and GoSquared to measure conversions and tune traffic sources.
A similar attack was clicked the same day by an admin at a Georgia organization.

The scam support number is personalized based on the user’s device IP and city. The same day, another admin at an Idaho district clicked another scareware variant.

This one was hosted on a normal web domain, rather than Azure’s *.web[.]core[.]windows[.]net. It makes use of the apiip.net API to fetch visitor IP addresses and will redirect the visitor if it falls within a certain range. This specifically is designed to hide from web crawlers, suggesting perhaps a malvertising origin.
On September 18th, an employee at a Texas organization clicked the below Outlook phishing attack.

This page offers the user options to login with Outlook, Office 365, Gmail, Yahoo, AOL or other mail, and it includes a two factor OTP prompt. It is likely hosted on a benign domain ‘comejoinus[.]de’ that has been compromised and is unwittingly hosting the phishing page. Based on the content, the delivery likely included an Adobe document share or ‘you’re invited’ lure.
We also saw sustained phishing attacks targeting personal accounts on work devices. On September 18, a staff member at a Florida organization clicked the below American Express phishing page.

Like other American Express phishing pages, it makes use of homoglyph characters (eg. AmeriÑÉn á¬â²press, UÑеr ID, etc) to evade detection. The page itself checks for the presence of a hash fragment in the URL, and otherwise redirects the request to a benign page.
The same day, an employee at a Georgia organization clicked on the below Netflix phishing attack.

The page makes use of .replit hosting for free TLS, uptime and reputation. The URL uses clever encodings to conceal references to the legitimate Netflix page and uses detection techniques to redirect potential scanners to the legitimate Netflix domain.
Mitigations
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Educate users about phishing risks even on pages that purport to use MFA
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
If you are interested in seeing how PIXM can help prevent attacks like these for your organization, book a demo here.
threatresearch@pixmsecurity.com

Recent Comments