TL;DR
- Someone tried accessing my work account (enabled with Authenticator)
- Within an hour, I received a Microsoft Outlook phishing attack in my work email
- Upon clicking on the link,
Pixm shut down the attack within one second in my browser - All major cybersecurity services marked this attack as safe
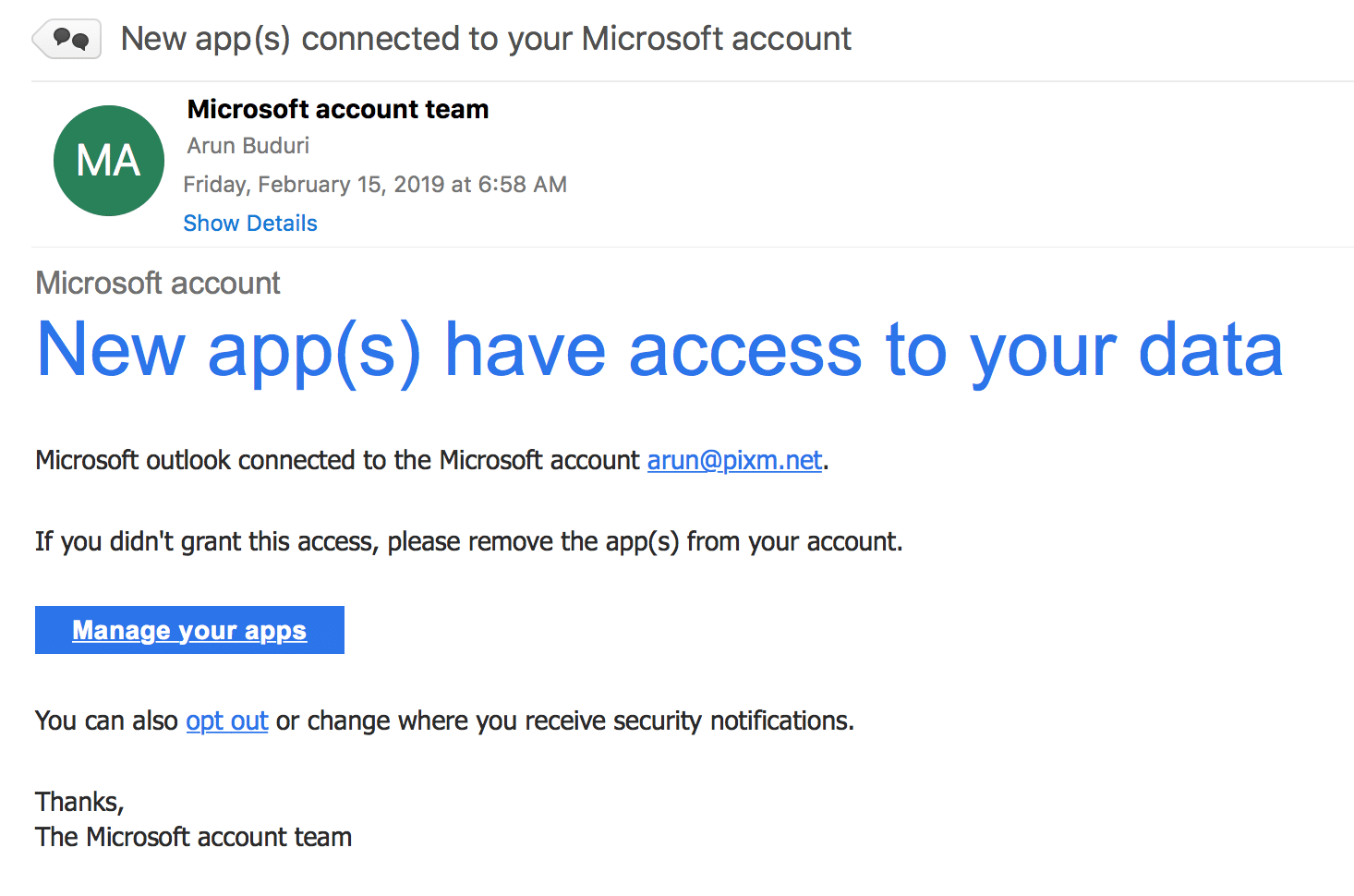
Early this morning, I got a notification in my Authenticator App that someone is requesting a login to my account. Shortly thereafter, I received a phishing email that looked like it was from Microsoft.
It’s easy enough to see this is a phishing email. The “Microsoft account team” FROM: address was my own email address. It wasn’t straight forward to find this out though since I had to hit REPLY to see the email address.
Hovering on the “Manage your apps” button revealed a link with a core.windows.net domain owned by Microsoft. This is a common technique used by attackers to use popular domains to host their phishing attacks.
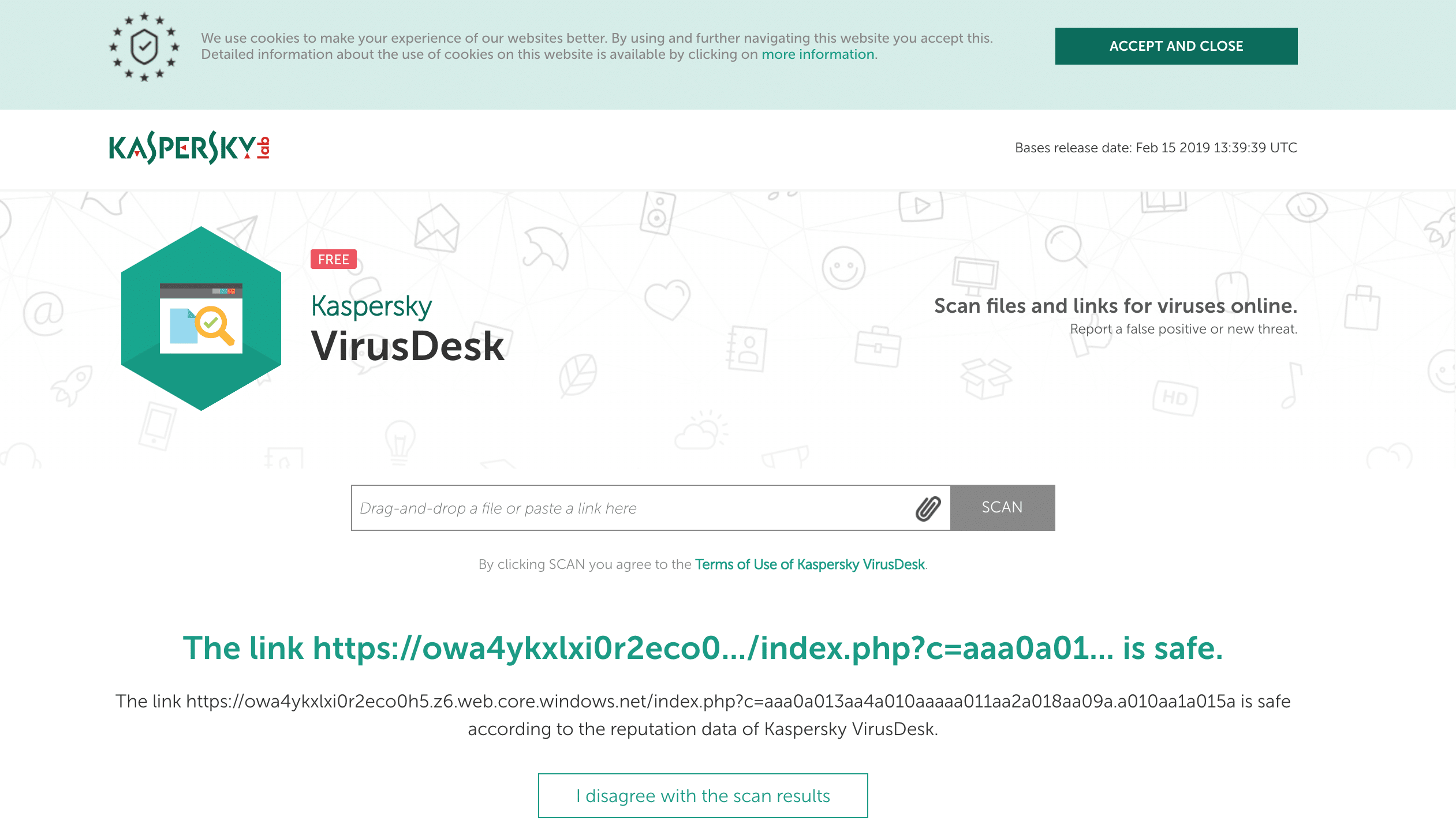
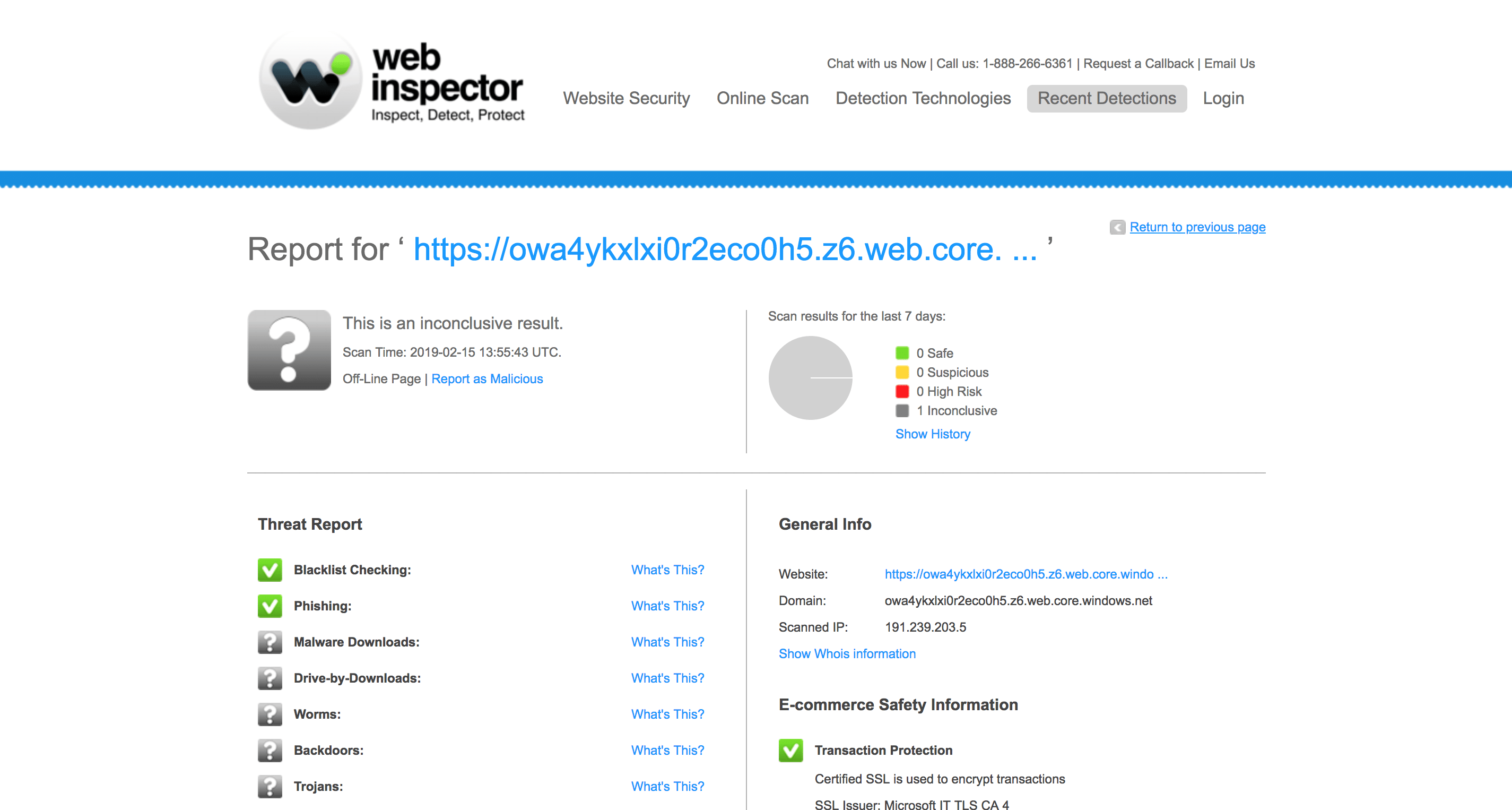
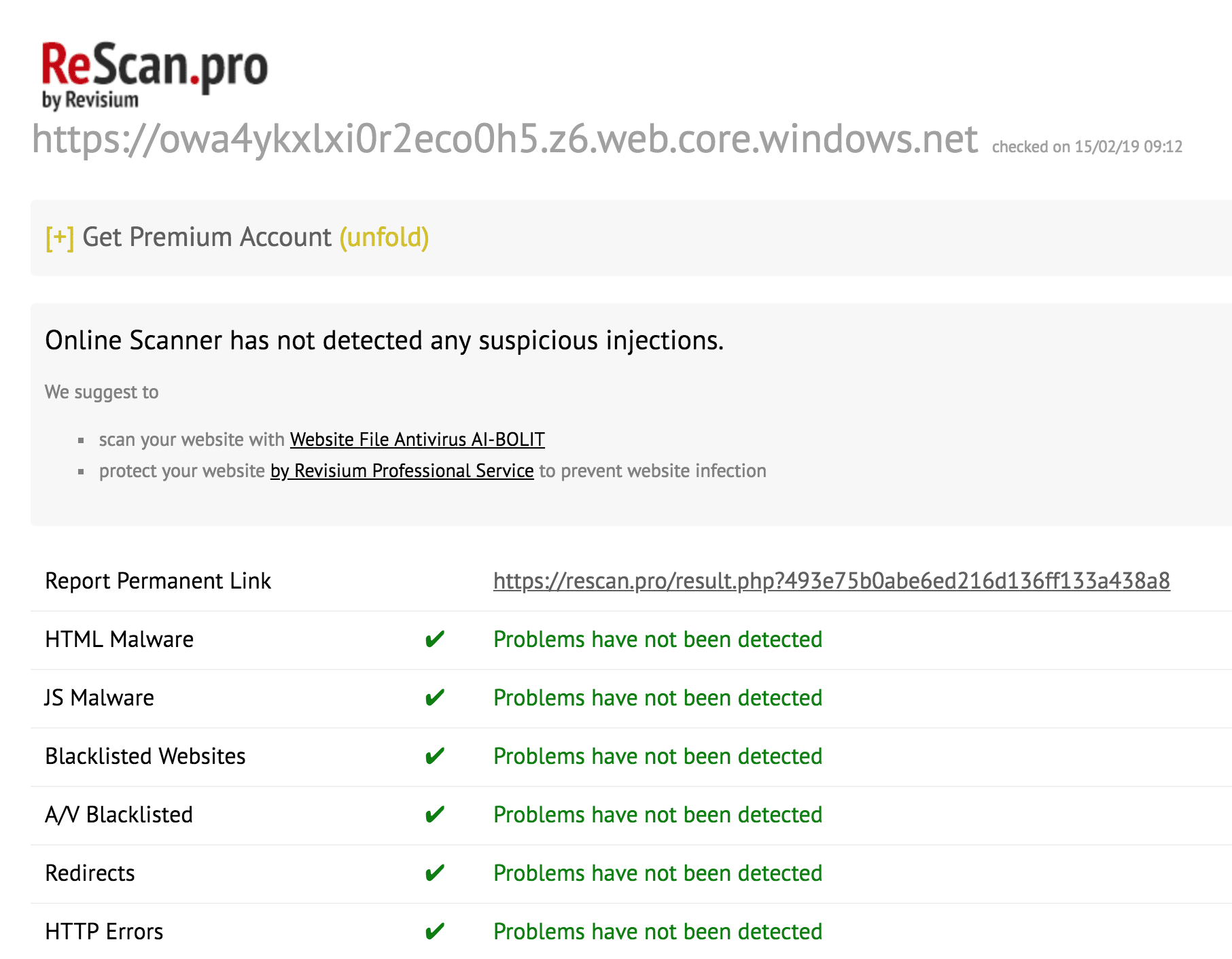
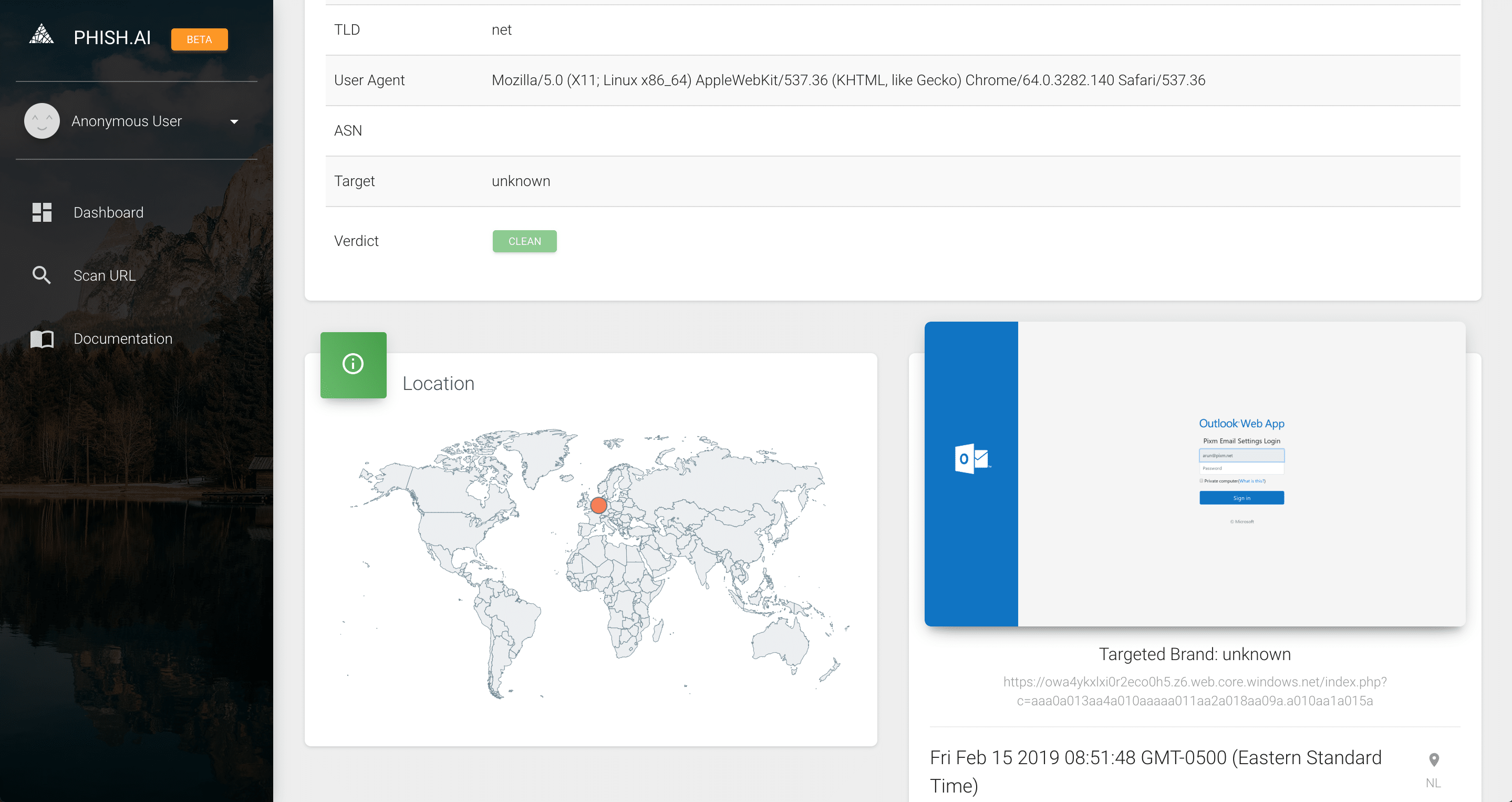
https : / / owa4ykxlxi0r2eco0h5.z6.web.core.windows.net / index.php?c=aaa0a013aa4a010aaaaa011aa2a018aa09a.a010aa1a015a
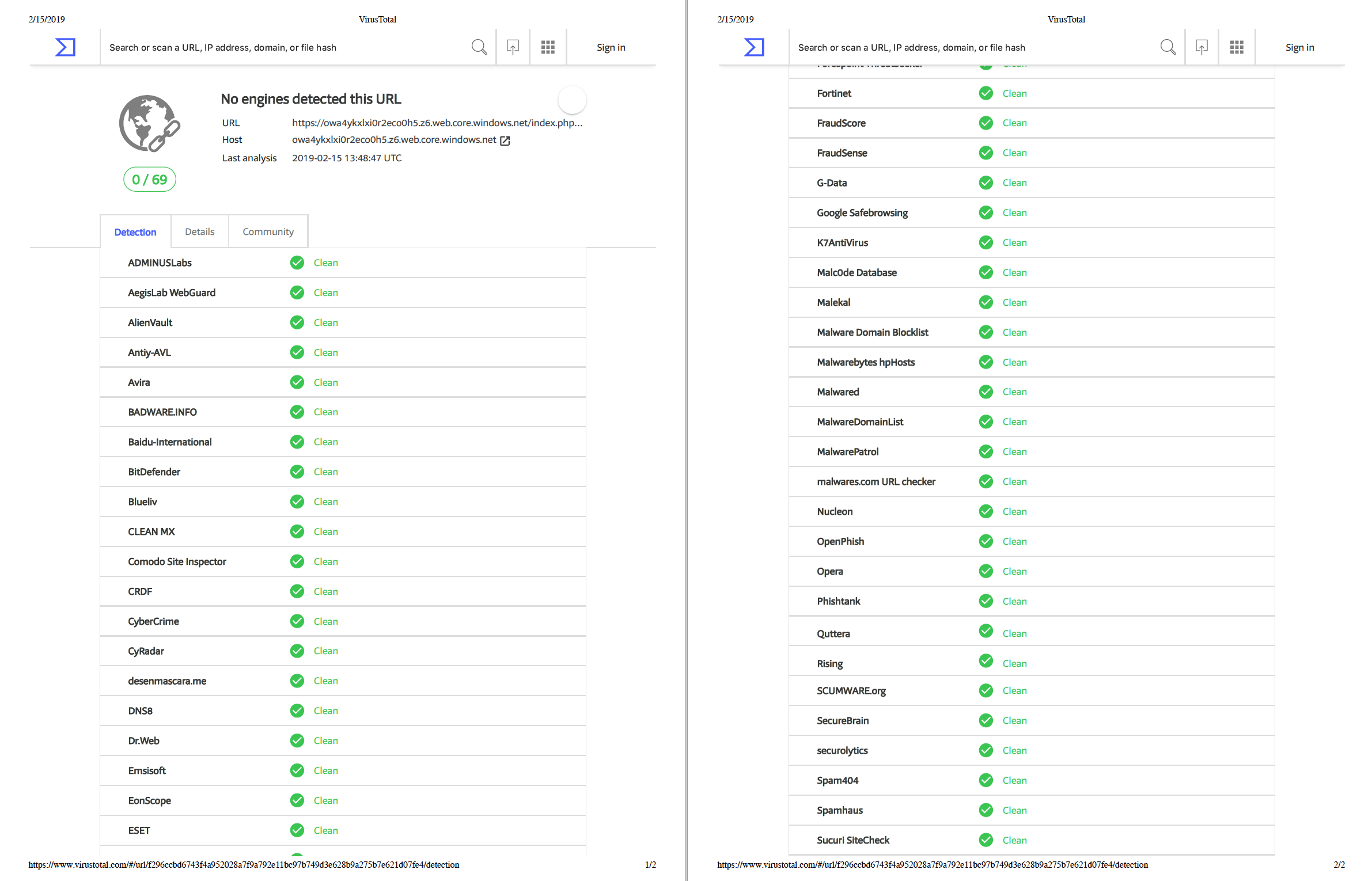
EDIT: 16 Feb 2019 8:30AM ET – As of this update, 24 hours since the attack, this link is blacklisted by only 3 out of 69 cybersecurity services.
With Pixm Anti-Phishing installed on my mac, I opened the link in my Chrome browser. Within a second of opening the page, Pixm detected it as a phishing attack and shut it down immediately.
Others Fail To Detect
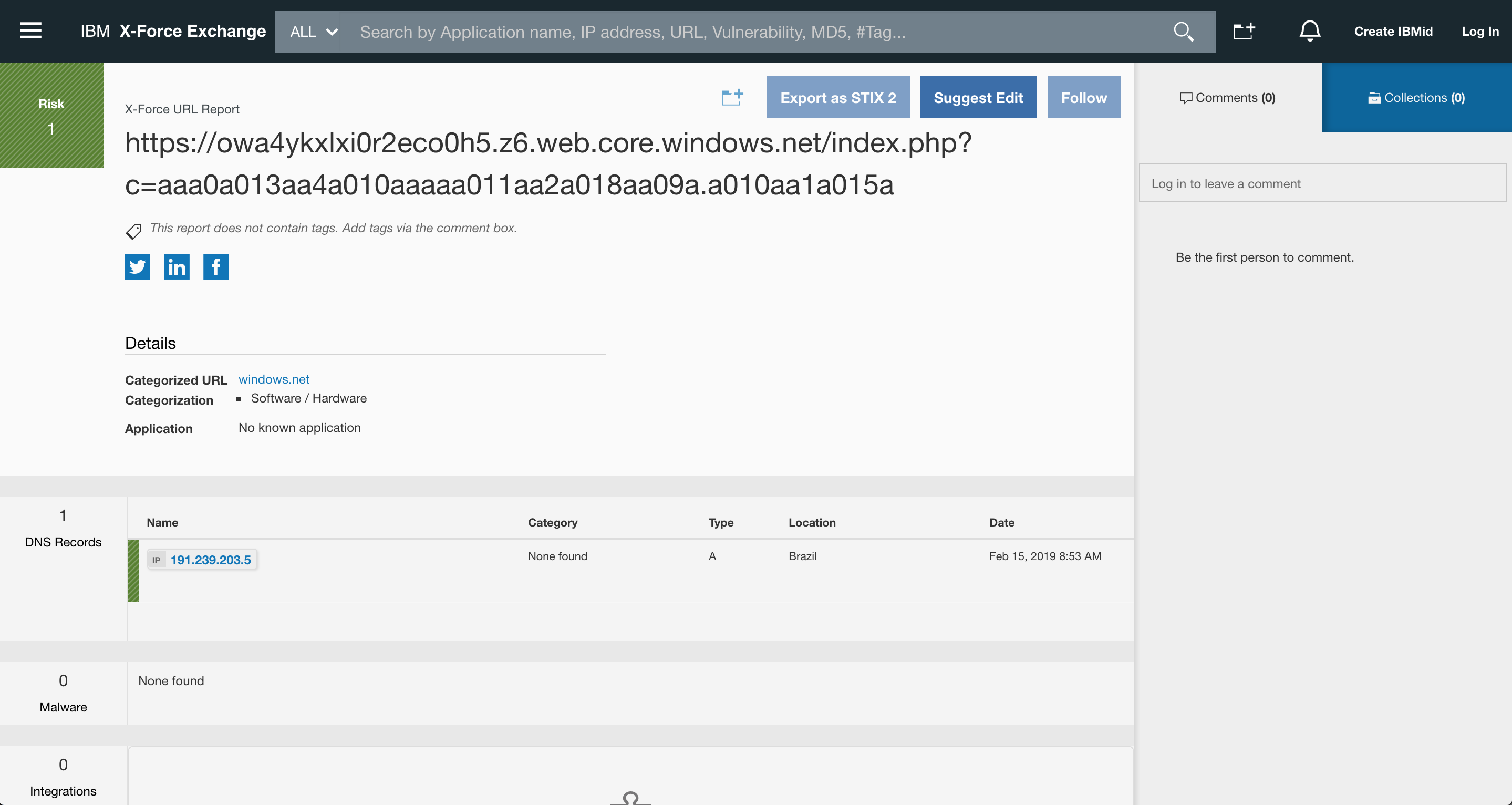
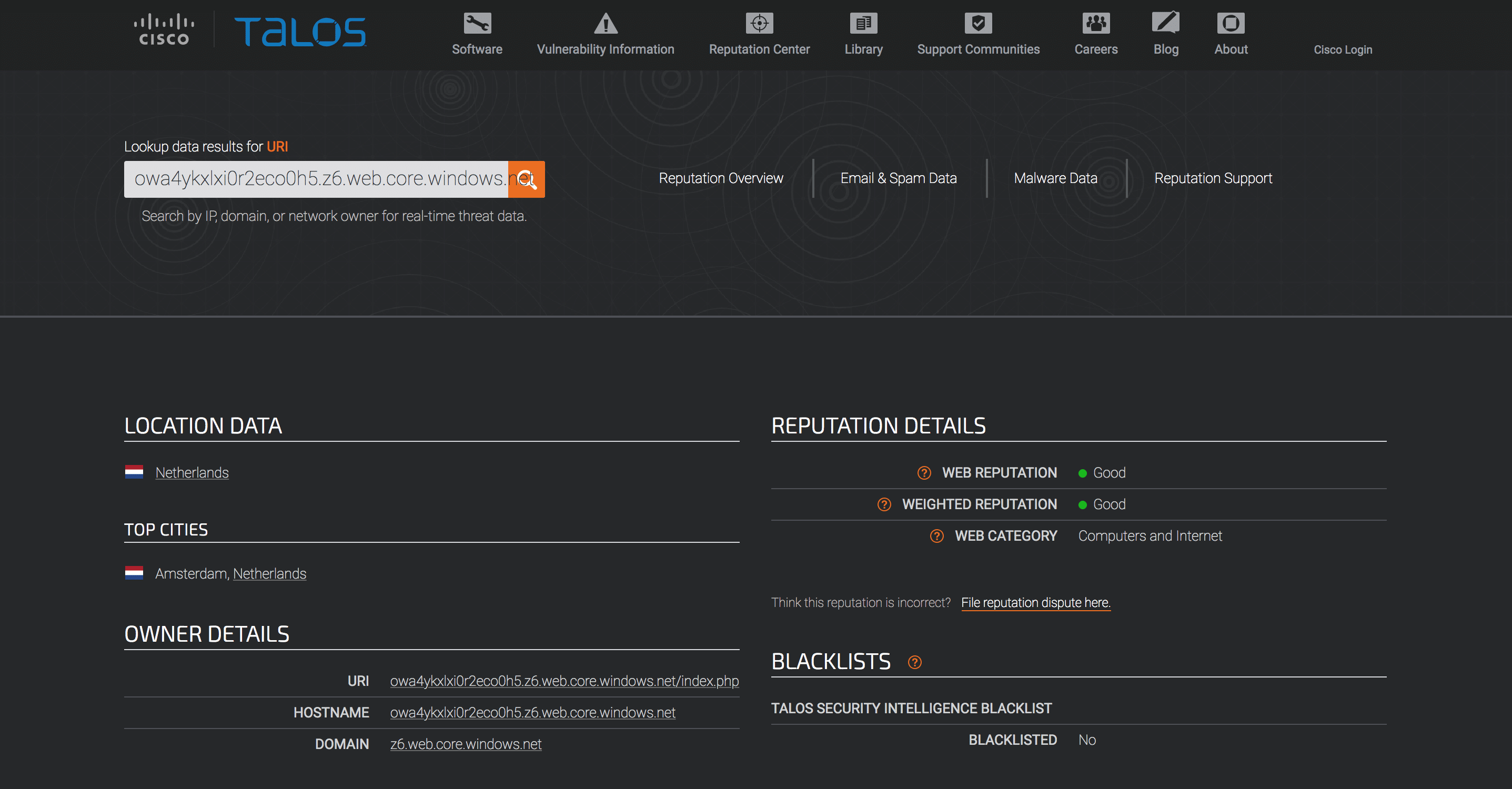
As you can see in the video, Microsoft, Google, WebOfTrust, Avast and McAfee SECURE fail to detect the attack. Below are some well-known URL scanning services failing to detect this attack.
VirusTotal
IBM X-Force
Cisco TALOS
Kaspersky
Comodo Web Inspector
ReScan PRO
Phish.AI

Recent Comments